Cloud Key Management
Manage encryption keys on Google Cloud.
Deliver scalable, centralized, fast cloud key management
Help satisfy compliance, privacy, and security needs
Apply hardware security modules (HSMs) effortlessly to your most sensitive data
Use an external KMS to protect your data in Google Cloud and separate the data from the key
Approve or deny any request for your encryption keys based on clear and precise justifications
Benefits
Scale your security globally
Scale your security globally
Scale your application to Google’s global footprint while letting Google worry about the challenges of key management, including managing redundancy, latency, and data residency.
Help achieve your compliance requirements
Help achieve your compliance requirements
Easily encrypt your data in the cloud using software-backed encryption keys, FIPS 140-2 Level 3 validated HSMs, customer-provided keys or an External Key Manager.
Leverage from integration with Google Cloud products
Leverage from integration with Google Cloud products
Use customer-managed encryption keys (CMEK) to control the encryption of data across Google Cloud products while benefiting from additional security features, such as Google Cloud IAM and audit logs.
Key features
Core features
Centrally manage encryption keys
A cloud-hosted key management service that lets you manage symmetric and asymmetric cryptographic keys for your cloud services the same way you do on-premises. You can generate, use, rotate, and destroy AES256, RSA 2048, RSA 3072, RSA 4096, EC P256, and EC P384 cryptographic keys.
Deliver hardware key security with HSM
Host encryption keys and perform cryptographic operations in FIPS 140-2 Level 3 validated HSMs. With this fully managed service, you can protect your most sensitive workloads without the need to worry about the operational overhead of managing an HSM cluster.
Provide support for external keys with EKM
Encrypt data in integrated Google services with encryption keys that are stored and managed in a third-party key management system that’s deployed outside Google’s infrastructure. External Key Manager allows you to maintain separation between your data at rest and your encryption keys while still leveraging the power of cloud for compute and analytics.
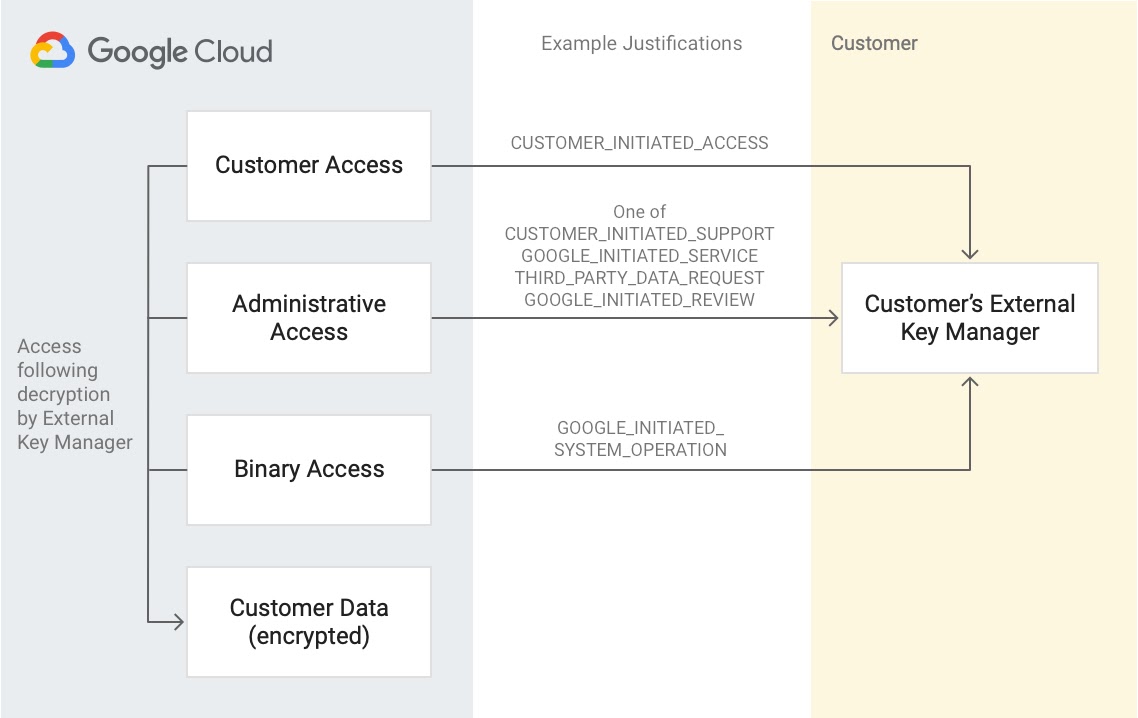
Be the ultimate arbiter of access to your data
Key Access Justifications works with Cloud EKM to greatly advance the control you have over your data. It’s the only product that gives you visibility into every request for an encryption key, a justification for that request, and a mechanism to approve or deny decryption in the context of that request. These controls are covered by Google’s integrity commitments.
Documentation
Documentation
Use cases
Use cases
Support regulatory compliance
Cloud KMS, together with Cloud HSM and Cloud EKM, supports a wide range of compliance mandates that call for specific key management procedures and technologies. It does so in a scalable, cloud-native way, without undermining the agility of the cloud implementation. Various mandates call for hardware encryption (HSM), keys being separated from data (EKM), or keys being handled securely (KMS overall). Key management is compliant with FIPS 140-2.
Manage encryption keys via secure hardware
Customers who are subject to compliance regulations may be required to store their keys and perform crypto operations in a FIPS 140-2 Level 3 validated device. By allowing customers to store their keys in a FIPS validated HSM, they are able to meet their regulator’s demand and maintain compliance in the cloud. This is also critical for customers seeking a level of assurance that the cloud provider cannot see or export their key material.
Manage encryption keys outside the cloud
Customers subject to regulatory or regional security requirements need to adopt cloud computing while retaining the encryption keys in their possession. External Key Manager allows them to maintain separation between data at rest and encryption keys while still leveraging the power of cloud for compute and analytics. This is accomplished with full visibility into who has access to the keys, when they have been used, and where they are located.
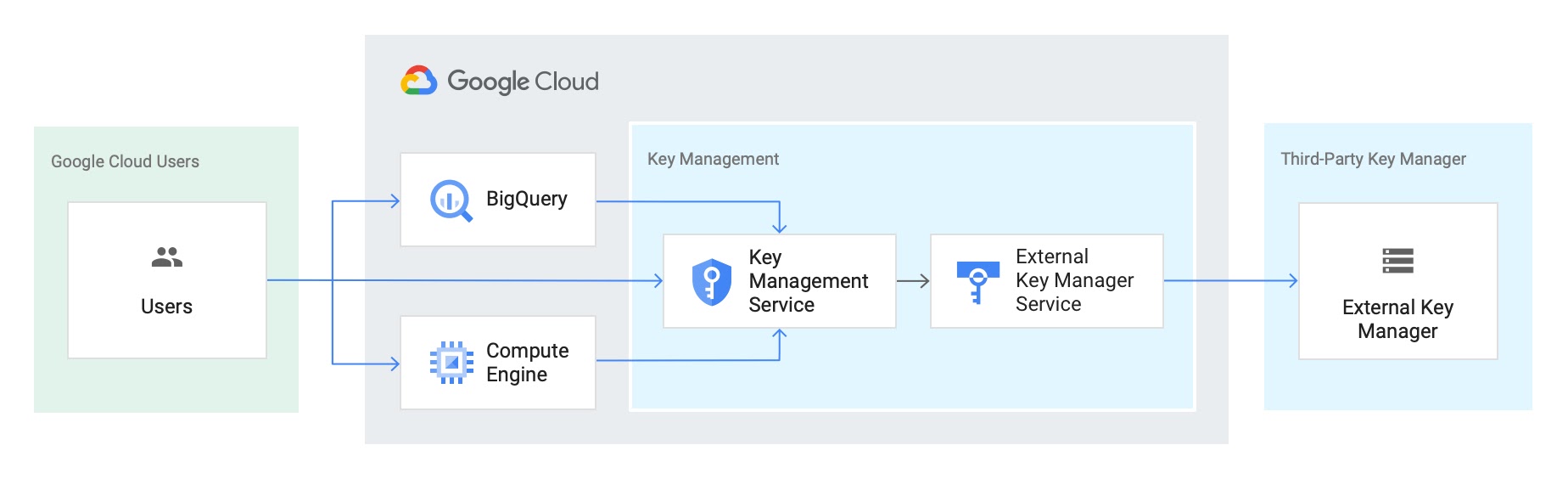
Key Access Justifications and EKM data flow
Key Access Justifications gives Google Cloud customers visibility into every request for an encryption key, a justification for that request, and a mechanism to approve or deny decryption in the context of that request. The use cases focus on both enforcement and visibility for data access.
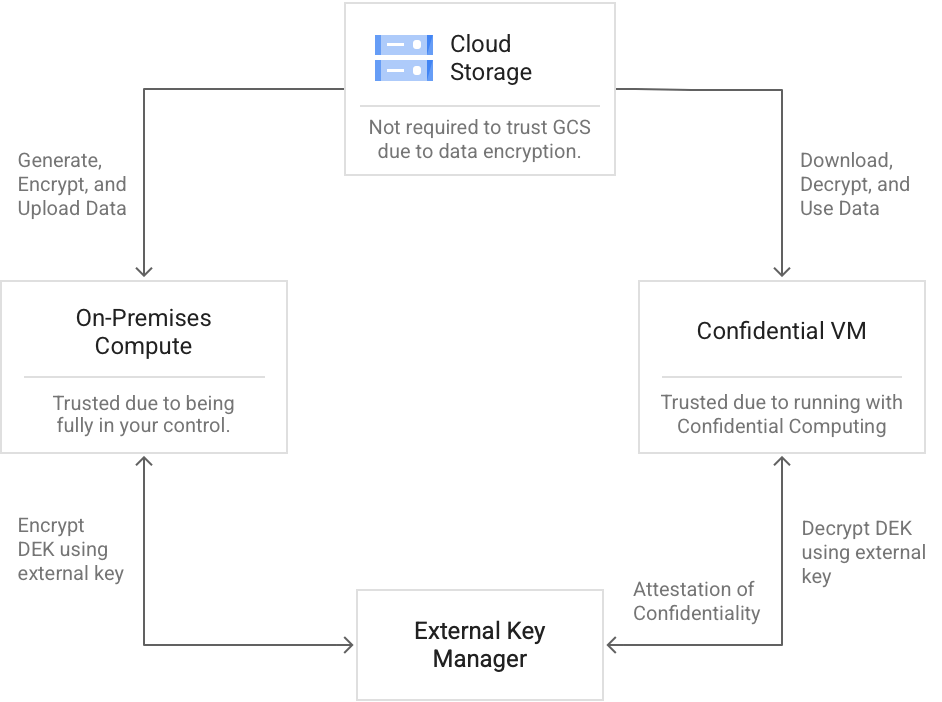
Ubiquitous data encryption
Seamlessly encrypt data as it is sent to the cloud, using your external key management solution, in a way that only a confidential VM service can decrypt and compute on it.
All features
All features
| Symmetric and asymmetric key support | Cloud KMS allows you to create, use, rotate, automatically rotate, and destroy AES256 symmetric and RSA 2048, RSA 3072, RSA 4096, EC P256, and EC P384 asymmetric cryptographic keys. With HSM, encrypt, decrypt, and sign with AES-256 symmetric and RSA 2048, RSA 3072, RSA 4096, EC P256, and EC P384 asymmetric cryptographic keys. |
| Create external keys with EKM | Generate your external key using one of the following external key managers: Equinix, Fortanix, Ionic, Thales, and Unbound. Once you have linked your external key with Cloud KMS, you can use it to protect data at rest in BigQuery and Compute Engine. |
| Delay for key destruction | Cloud KMS has a built-in 24-hour delay for key material destruction, to prevent accidental or malicious data loss. |
| Encrypt and decrypt via API | Cloud KMS is a REST API that can use a key to encrypt, decrypt, or sign data, such as secrets for storage. |
| High global availability | Cloud KMS is available in several global locations and across multi-regions, allowing you to place your service where you want for low latency and high availability. |
| Automated and at-will key rotation | Cloud KMS allows you to set a rotation schedule for symmetric keys to automatically generate a new key version at a fixed time interval. Multiple versions of a symmetric key can be active at any time for decryption, with only one primary key version used for encrypting new data. With EKM, create an externally managed key directly from the Cloud KSM console. |
| Statement attestation with HSM | With Cloud HSM, verify that a key was created in the HSM with attestation tokens generated for key creation operations. |
| Integration with GKE | Encrypt Kubernetes secrets at the application-layer in GKE with keys you manage in Cloud KMS. In addition, you can store API keys, passwords, certificates, and other sensitive data with the Secret Manager storage system. |
| Maintain key-data separation | With EKM, maintain separation between your data at rest and your encryption keys while still leveraging the power of cloud for compute and analytics. |
| Key data residency | If using Cloud KMS, your cryptographic keys will be stored in the region where you deploy the resource. You also have the option of storing those keys inside a physical Hardware Security Module located in the region you choose with Cloud HSM. |
| Key import | You may be using existing cryptographic keys that were created on your premises or in an external key management system. You can import them into Cloud HSM keys or import software keys into Cloud KMS. |
| Justified access | Get a clear reason for every decryption request that will cause your data to change state from at-rest to in-use with Key Access Justifications. |
| Automated policy | Key Access Justifications lets you set automated policies that approve or deny access to keys based on specific justifications. Let your external key manager, provided by Google Cloud technology partners, take care of the rest. |
| Integrity commitment | Controls provided by Key Access Justifications are covered by Google’s integrity commitments, so that you know they can be trusted. |
Pricing
Pricing
Cloud Key Management Service charges for usage and varies based on the following products: Cloud Key Management Service, Cloud External Key Manager, and Cloud HSM.
Product | Price (US$) |
|---|---|
Cloud KMS: active key versions | $0.06 per month |
Cloud KMS: key use operations (Encrypt/Decrypt) | $0.03 per 10,000 operations |
Cloud KMS: key admin operations | free |
Cloud HSM: key versions (AES256, RSA2048) | $1.00 per month |
Cloud HSM: key versions (RSA 3072, RSA 4096) | 0–2,000 key versions: $2.50 per month 2,001+ key versions: $1.00 per month |
Cloud HSM: key versions (EC P256, EC P384) | 0–2,000 key versions: $2.50 per month 2,001+ key versions: $1.00 per month |
Cloud EKM: key versions | $3.00 per month |
Cloud EKM: key use operations | $0.03 per 10,000 operations |
If you pay in a currency other than USD, the prices listed in your currency on Google Cloud SKUs apply.
Take the next step
Start building on Google Cloud with $300 in free credits and 20+ always free products.
Need help getting started?
Contact salesWork with a trusted partner
Find a partnerContinue browsing
See all products