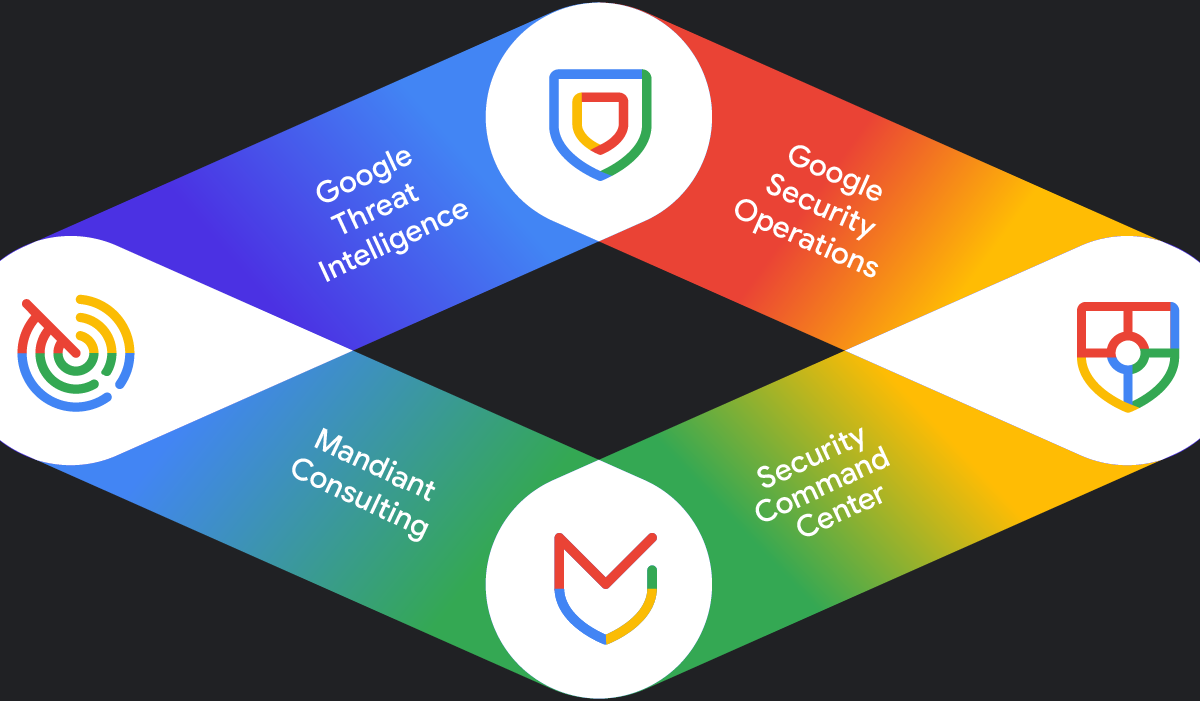
Gain the Google Cloud Security advantage
Gain the Google Cloud Security advantage
Google’s security strengths are your powerful security advantages: built-in, AI-driven protection that uses our vast global threat intelligence to detect, prevent, and respond to threats at scale. Secure your business on our secure-by-design cloud platform and leverage Google Security Operations and Mandiant expertise for proactive, accelerated defense, investigation, and response.
Get actionable threat intelligence at Google scale
Uncover and understand threats faster with unmatched global visibility. Google Threat Intelligence combines Mandiant’s frontline expertise, Google’s protection of billions of users and devices, and VirusTotal’s crowdsourced insights to deliver the world’s most comprehensive view of the threat landscape. With AI-powered analysis from Gemini, you get faster summaries, tailored insights, and code behavior explanations—turning intelligence into actionable defense at scale.
Stay ahead of threats with AI-powered security operations
Detect, investigate, and respond to threats at Google speed and scale. Google Security Operations ingests and analyzes your data on a planetary scale, applying Google’s threat intelligence and 4,000+ curated detections to uncover even the most novel threats. With AI-powered capabilities from Gemini, teams can surface critical context, generate detections and playbooks, and reduce operational toil—all while retaining data longer for effective threat hunting and faster decision-making. Google Unified Security is a context-aware security solution designed to deliver integrated, intelligence-driven, and AI-infused security workflows through Gemini.
Secure your AI innovation on the most trusted cloud
Run your business and AI workloads on a secure-by-design foundation, with core infrastructure designed, built, and operated with security in mind. Our cloud and enterprise browsing platforms offer built-in security and compliance capabilities, so enterprises can achieve a strong security posture. Manage your business with fewer vulnerabilities, protect users and workloads from emerging threats, and maintain digital sovereignty with our cloud security services.
Get expert help when you need it most with Mandiant
To fully realize Google as an extension of your security team, Mandiant experts are there when customers need them most: before, during, and after a breach. Our Mandiant incident response and consulting teams bring unparalleled frontline experience: more than 450,000 hours investigating security incidents last year, including some of the world’s largest and most impactful. These renowned experts provide strategic and technical defense, helping you prepare for and recover from critical cybersecurity incidents and get back to business quickly.
Accelerate your AI transformation
Accelerate your AI transformation
Google Cloud enables you to both secure your AI innovation and empower your defenders with AI-powered security operations. And we are committed to making our platform the safest place for you to build, deploy, and run AI workloads securely, privately, and compliantly.
Secure the entire AI stack and life cycle
Google Cloud's AI Protection secures your AI journey from development to deployment and beyond, discovering and safeguarding models, agents, applications, and data with tailored controls and policies. Tools like Model Armor protect models from adversarial attacks like prompt injection, while Security Command Center gives a unified view of your security posture, helping teams detect and respond to threats across all workloads—including AI systems. Together, they ensure your AI initiatives are resilient, compliant, and trustworthy across the entire life cycle.
Transform SecOps with Agentic SOC
Agentic SOC combines AI-driven automation with human expertise to transform security operations. AI agents continuously triage alerts, investigate threats, and manage repetitive tasks, freeing teams to focus on complex, high-priority risks. By reducing alert fatigue and accelerating response, Agentic SOC builds a smarter, more resilient defense—bringing the future of human-led, AI-powered security to your organization.
Adopt AI with guidance from Mandiant
Mandiant AI Security Consulting Solutions helps your organization securely integrate AI and leverage it for robust cyber defenses. Our experts offer AI security assessments, red teaming against generative AI models and applications, and integrate AI into your operations to reduce manual toil and build advanced threat detections.
Accelerate responsible AI deployment using SAIF
Google’s Secure AI Framework (SAIF) is designed to address top-of-mind concerns for security professionals, like AI/ML model risk management, security, and privacy—helping ensure AI systems are secure-by-default from the start. To make adoption easier, we created SAIF.google, including a SAIF Risk Self Assessment, so organizations can put SAIF into practice and build and deploy AI responsibly.
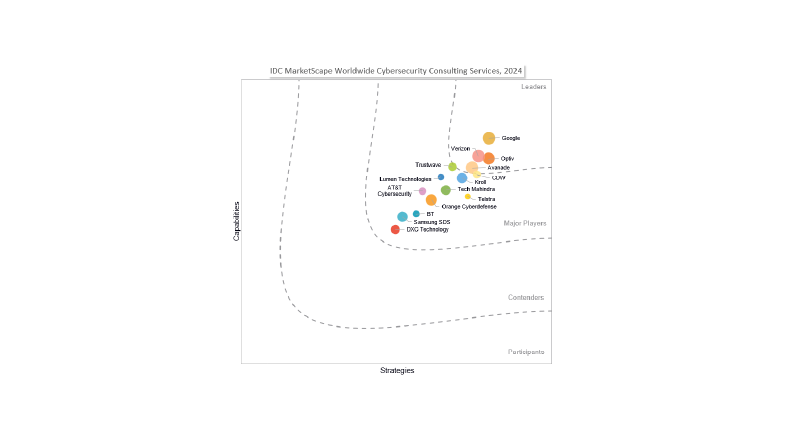
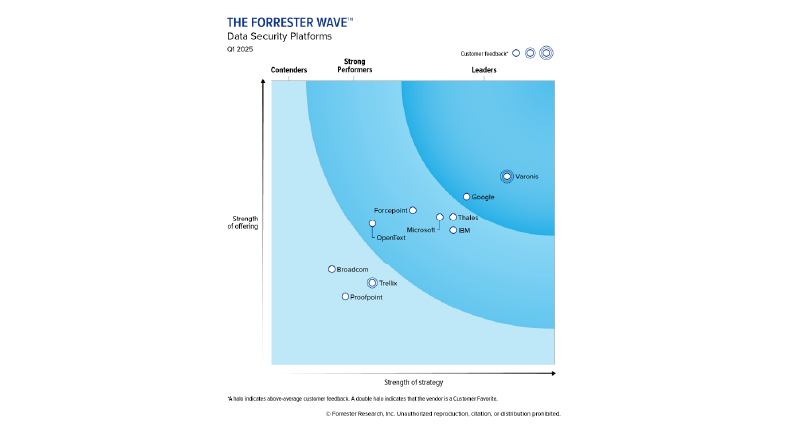
Trusted by leading organizations
Trusted by leading organizations
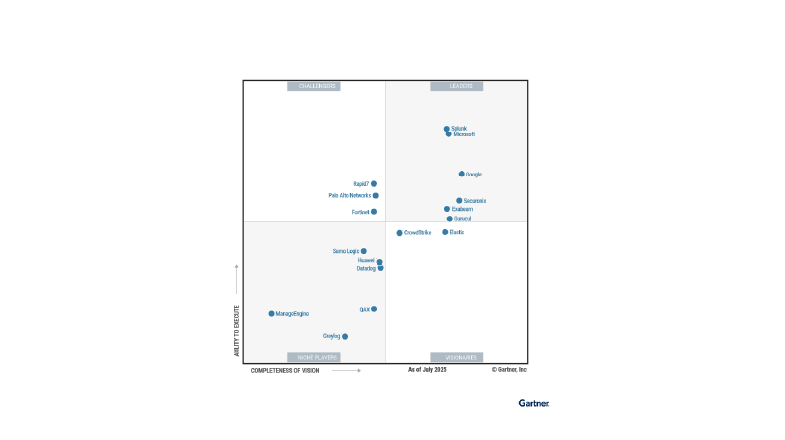
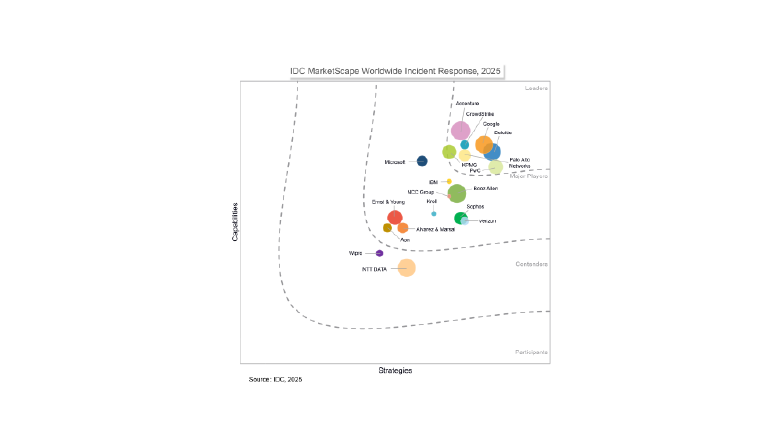
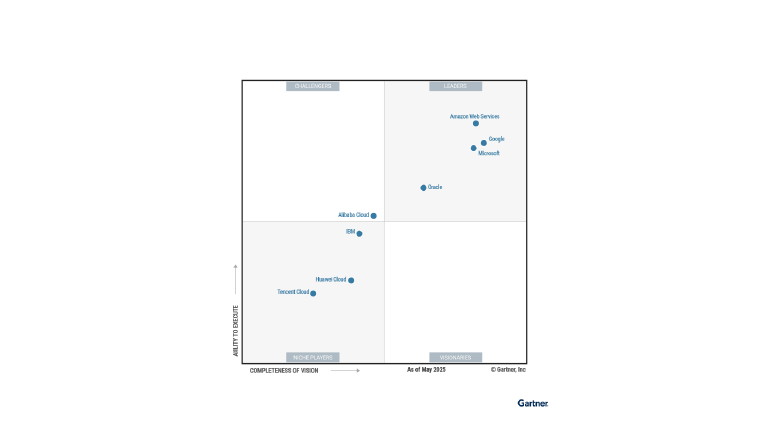
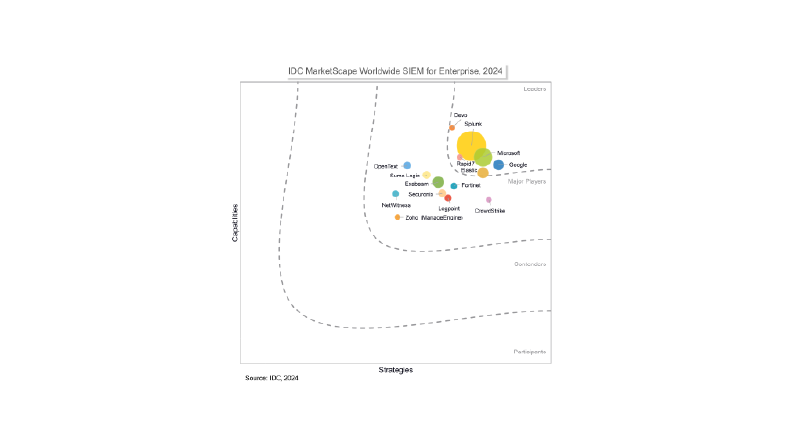
Recognized by industry analysts
Recognized by industry analysts
Browse resources
 Google Cloud Security blogNews, tips, and inspiration to accelerate your security and AI transformation.
Google Cloud Security blogNews, tips, and inspiration to accelerate your security and AI transformation.5-min read
Read the blog Google Threat Intelligence blogThe latest frontline investigations, analysis, and in-depth security research from Mandiant experts.
Google Threat Intelligence blogThe latest frontline investigations, analysis, and in-depth security research from Mandiant experts.5-min read
Read the blog Google Cloud Security Community blogInsights, answers, and expert perspectives to optimize your security tools, from Googlers and seasoned users.
Google Cloud Security Community blogInsights, answers, and expert perspectives to optimize your security tools, from Googlers and seasoned users.5-min read
Read the blog
 Cloud Security PodcastAnton Chuvakin and Timothy Peacock tackle today’s most interesting cloud security stories, including what we’re doing at Google Cloud. Come for the no-nonsense insights; stay for the threat model questioning and bad puns.
Cloud Security PodcastAnton Chuvakin and Timothy Peacock tackle today’s most interesting cloud security stories, including what we’re doing at Google Cloud. Come for the no-nonsense insights; stay for the threat model questioning and bad puns.5-min read
Listen now The Defender’s Advantage PodcastLuke McNamara is joined by fellow cybersecurity experts providing frontline insights into the latest attacks, threat research, and trends. Dive deep on nation-state activity, malware, and more.
The Defender’s Advantage PodcastLuke McNamara is joined by fellow cybersecurity experts providing frontline insights into the latest attacks, threat research, and trends. Dive deep on nation-state activity, malware, and more.5-min read
Listen now Behind the Binary PodcastGoogle FLARE team member Josh Stroschein uncovers the human stories and unique perspectives of the experts who secure our digital world through reverse engineering.
Behind the Binary PodcastGoogle FLARE team member Josh Stroschein uncovers the human stories and unique perspectives of the experts who secure our digital world through reverse engineering.5-min read
Listen now
 The Defender's AdvantageA guide to activating cyber defense.
The Defender's AdvantageA guide to activating cyber defense.5-min read
Read the report The Total Economic Impact™ of Google Security OperationsAn in-depth Forrester Consulting study.
The Total Economic Impact™ of Google Security OperationsAn in-depth Forrester Consulting study.5-min read
Read the report Cybersecurity Forecast 2026Forward-looking insights to plan for the year ahead.
Cybersecurity Forecast 2026Forward-looking insights to plan for the year ahead.5-min read
Read the report
 Google Cloud Next 2026Save the date for Next ‘26: April 22-24, 2026, at Mandalay Bay Convention Center in Las Vegas.
Google Cloud Next 2026Save the date for Next ‘26: April 22-24, 2026, at Mandalay Bay Convention Center in Las Vegas.5-min read
Subscribe for updates Cyber Defense Summit 2025Stream keynotes and deep-dive sessions on securing AI innovation, building executive resilience, and countering today's most sophisticated cyber threats.
Cyber Defense Summit 2025Stream keynotes and deep-dive sessions on securing AI innovation, building executive resilience, and countering today's most sophisticated cyber threats.5-min read
Watch now Security TalksJoin our security experts in this ongoing series as they explore the latest AI innovations across our security product portfolio, threat intelligence best practices, and more.
Security TalksJoin our security experts in this ongoing series as they explore the latest AI innovations across our security product portfolio, threat intelligence best practices, and more.5-min read
Watch on-demand
 CISO Insights HubExpert perspectives, reports, and frameworks to help security leaders navigate today’s evolving threat landscape, with insights from Google Cloud’s Office of the CISO.
CISO Insights HubExpert perspectives, reports, and frameworks to help security leaders navigate today’s evolving threat landscape, with insights from Google Cloud’s Office of the CISO.5-min read
Learn more Board of Directors Insights HubInsights and best practices designed for boards to lead security decisions and ensure resilient, secure operations.
Board of Directors Insights HubInsights and best practices designed for boards to lead security decisions and ensure resilient, secure operations.5-min read
Learn more The Cyber Savvy BoardroomFrom Google Cloud's Office of the CISO, get monthly strategic insights from security leaders, executives, and board members to help you confidently shape your organization's security posture and future.
The Cyber Savvy BoardroomFrom Google Cloud's Office of the CISO, get monthly strategic insights from security leaders, executives, and board members to help you confidently shape your organization's security posture and future.Video (1:47)
Listen now
Blogs
 Google Cloud Security blogNews, tips, and inspiration to accelerate your security and AI transformation.
Google Cloud Security blogNews, tips, and inspiration to accelerate your security and AI transformation.5-min read
Read the blog Google Threat Intelligence blogThe latest frontline investigations, analysis, and in-depth security research from Mandiant experts.
Google Threat Intelligence blogThe latest frontline investigations, analysis, and in-depth security research from Mandiant experts.5-min read
Read the blog Google Cloud Security Community blogInsights, answers, and expert perspectives to optimize your security tools, from Googlers and seasoned users.
Google Cloud Security Community blogInsights, answers, and expert perspectives to optimize your security tools, from Googlers and seasoned users.5-min read
Read the blog
Podcasts
 Cloud Security PodcastAnton Chuvakin and Timothy Peacock tackle today’s most interesting cloud security stories, including what we’re doing at Google Cloud. Come for the no-nonsense insights; stay for the threat model questioning and bad puns.
Cloud Security PodcastAnton Chuvakin and Timothy Peacock tackle today’s most interesting cloud security stories, including what we’re doing at Google Cloud. Come for the no-nonsense insights; stay for the threat model questioning and bad puns.5-min read
Listen now The Defender’s Advantage PodcastLuke McNamara is joined by fellow cybersecurity experts providing frontline insights into the latest attacks, threat research, and trends. Dive deep on nation-state activity, malware, and more.
The Defender’s Advantage PodcastLuke McNamara is joined by fellow cybersecurity experts providing frontline insights into the latest attacks, threat research, and trends. Dive deep on nation-state activity, malware, and more.5-min read
Listen now Behind the Binary PodcastGoogle FLARE team member Josh Stroschein uncovers the human stories and unique perspectives of the experts who secure our digital world through reverse engineering.
Behind the Binary PodcastGoogle FLARE team member Josh Stroschein uncovers the human stories and unique perspectives of the experts who secure our digital world through reverse engineering.5-min read
Listen now
Reports
 The Defender's AdvantageA guide to activating cyber defense.
The Defender's AdvantageA guide to activating cyber defense.5-min read
Read the report The Total Economic Impact™ of Google Security OperationsAn in-depth Forrester Consulting study.
The Total Economic Impact™ of Google Security OperationsAn in-depth Forrester Consulting study.5-min read
Read the report Cybersecurity Forecast 2026Forward-looking insights to plan for the year ahead.
Cybersecurity Forecast 2026Forward-looking insights to plan for the year ahead.5-min read
Read the report
Events
 Google Cloud Next 2026Save the date for Next ‘26: April 22-24, 2026, at Mandalay Bay Convention Center in Las Vegas.
Google Cloud Next 2026Save the date for Next ‘26: April 22-24, 2026, at Mandalay Bay Convention Center in Las Vegas.5-min read
Subscribe for updates Cyber Defense Summit 2025Stream keynotes and deep-dive sessions on securing AI innovation, building executive resilience, and countering today's most sophisticated cyber threats.
Cyber Defense Summit 2025Stream keynotes and deep-dive sessions on securing AI innovation, building executive resilience, and countering today's most sophisticated cyber threats.5-min read
Watch now Security TalksJoin our security experts in this ongoing series as they explore the latest AI innovations across our security product portfolio, threat intelligence best practices, and more.
Security TalksJoin our security experts in this ongoing series as they explore the latest AI innovations across our security product portfolio, threat intelligence best practices, and more.5-min read
Watch on-demand
For the CISO
 CISO Insights HubExpert perspectives, reports, and frameworks to help security leaders navigate today’s evolving threat landscape, with insights from Google Cloud’s Office of the CISO.
CISO Insights HubExpert perspectives, reports, and frameworks to help security leaders navigate today’s evolving threat landscape, with insights from Google Cloud’s Office of the CISO.5-min read
Learn more Board of Directors Insights HubInsights and best practices designed for boards to lead security decisions and ensure resilient, secure operations.
Board of Directors Insights HubInsights and best practices designed for boards to lead security decisions and ensure resilient, secure operations.5-min read
Learn more The Cyber Savvy BoardroomFrom Google Cloud's Office of the CISO, get monthly strategic insights from security leaders, executives, and board members to help you confidently shape your organization's security posture and future.
The Cyber Savvy BoardroomFrom Google Cloud's Office of the CISO, get monthly strategic insights from security leaders, executives, and board members to help you confidently shape your organization's security posture and future.Video (1:47)
Listen now
Join our security community to build skills and share insights
Google Cloud Security CommunityExplore best practices for supporting your security and compliance objectives
Security best practices centerEvolve your organization's cybersecurity skills with Mandiant Academy
Browse available courses