Google Cloud Armor
Help protect your applications and websites against denial of service and web attacks.
Benefit from DDoS protection and WAF at Google scale
Detect and mitigate attacks against your Cloud Load Balancing workloads or VMs
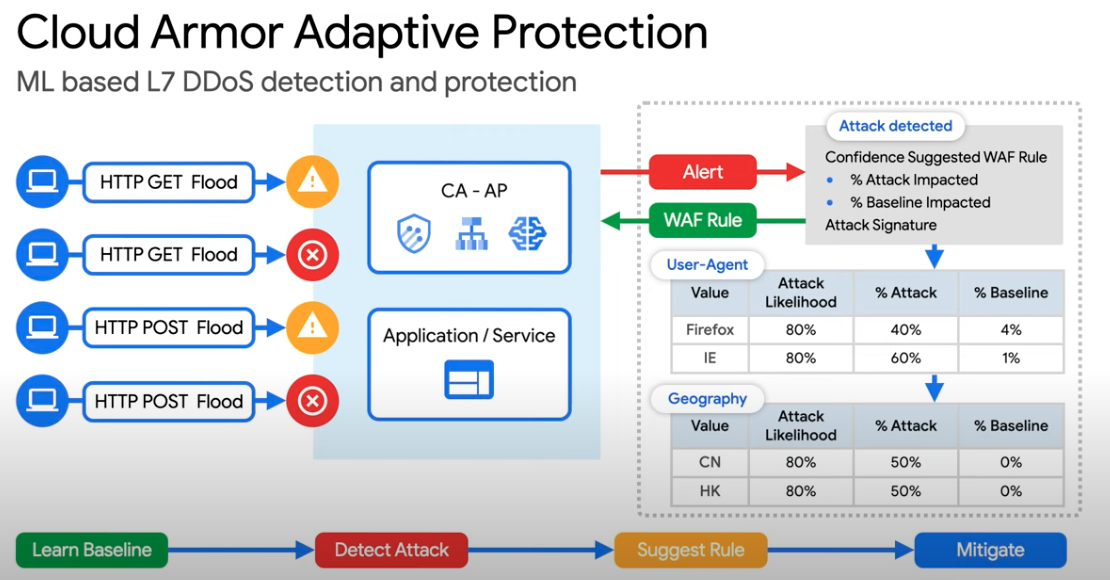
Adaptive Protection ML-based mechanism to help detect and block Layer 7 DDoS attacks
Mitigate OWASP Top 10 risks and help protect workloads on-premises or in the cloud
Bot management to stop fraud at the edge through native integration with reCAPTCHA Enterprise
Benefits
Built-in DDoS defense
Built-in DDoS defense
Cloud Armor benefits from our experience of protecting key internet properties, such as Google Search, Gmail, and YouTube. It provides built-in defenses against L3 and L4 DDoS attacks.
Mitigate OWASP Top 10 risks
Mitigate OWASP Top 10 risks
Cloud Armor provides predefined rules to help defend against attacks, such as cross-site scripting (XSS) and SQL injection (SQLi) attacks.
Enterprise-grade protection
Enterprise-grade protection
With Cloud Armor Enterprise tier, you will get access to DDoS and WAF services, curated rule sets, and other services for a predictable monthly price.
Key features
Key features
Adaptive protection
Automatically detect and help mitigate high volume Layer 7 DDoS attacks with an ML system trained locally on your applications. Learn more.
Advanced network DDoS protection
Always-on attack detection and mitigation to defend against volumetric network and protocol DDoS attacks to workloads using external network load balancers, protocol forwarding, and VMs with Public IP addresses. Learn more.
Pre-configured WAF rules
Out-of-the-box rules based on industry standards to mitigate against common web-application vulnerabilities and help provide protection from the OWASP Top 10. Learn more in our WAF rules guide.
Bot management
Provides automated protection for your apps from bots and helps stop fraud in line and at the edge through native integration with reCAPTCHA Enterprise. Learn more.
Rate limiting
Rate-based rules help you protect your applications from a large volume of requests that flood your instances and block access for legitimate users. Learn more.
What's new
What's new
Sign up for Google Cloud newsletters to receive product updates, event information, special offers, and more.
Documentation
Documentation
Cloud Armor overview
Learn how Cloud Armor works and see an overview of Cloud Armor features and capabilities.
Hands-on lab: Application load balancer with Cloud Armor
Learn how to configure an HTTP load balancer with global back ends, stress test the load balancer, and denylist the stress test IP.
Cloud Armor security policy overview
Use Google Cloud Armor security policies to help protect your load-balanced applications from distributed denial of service (DDoS) and other web-based attacks.
Cloud Armor Enterprise
Cloud Armor Enterprise helps protect your web applications and services from distributed denial-of-service (DDoS) attacks and other threats from the internet.
Bot management
Provides effective management of automated clients' requests toward your back ends through native integration with reCAPTCHA Enterprise.
Rate limiting
Rate-based rules help you protect your applications from a large volume of requests that flood your instances and block access for legitimate users.
Configuring Google Cloud Armor security policies
Use these instructions to filter incoming traffic to application load balancer by creating Google Cloud Armor security policies.
Configuring Google Cloud Armor through GKE Ingress
Learn how to use a BackendConfig custom resource to configure Google Cloud Armor in Google Kubernetes Engine (GKE).
Tuning Google Cloud Armor WAF rules
Preconfigured web application firewall (WAF) rules with dozens of signatures that are compiled from open source industry standards.
Not seeing what you’re looking for?
All features
All features
| Pre-defined WAF rules to mitigate OWASP Top 10 risks | Out-of-the-box rules based on industry standards to mitigate against common web-application vulnerabilities and help provide protection from the OWASP Top 10. |
| Rich rules language for web application firewall | Create custom rules using any combination of L3–L7 parameters and geolocation to help protect your deployment with a flexible rules language. |
| Visibility and monitoring | Easily monitor all of the metrics associated with your security policies in the Cloud Monitoring dashboard. You can also view suspicious application traffic patterns from Cloud Armor directly in the Security Command Center dashboard. |
| Logging | Get visibility into Cloud Armor decisions as well as the implicated policies and rules on a per-request basis via Cloud Logging. |
| Preview mode | Deploy Cloud Armor rules in preview mode to understand rule efficacy and impact on production traffic before enabling active enforcement. |
| Policy framework with rules | Configure one or more security policies with a hierarchy of rules. Apply a policy at varying levels of granularity to one or many workloads. |
| IP-based and geo-based access control | Filter your incoming traffic based on IPv4 and IPv6 addresses or CIDRs. Identify and enforce access control based on geographic location of incoming traffic. |
| Support for hybrid and multicloud deployments | Help defend applications from DDoS or web attacks and enforce Layer 7 security policies whether your application is deployed on Google Cloud or in a hybrid or multicloud architecture. |
| Named IP Lists | Allow or deny traffic through a Cloud Armor security policy based on a curated Named IP List. |
Pricing
Pricing
Google Cloud Armor is offered in two service tiers, Standard and Cloud Armor Enterprise.
A product or feature listed on this page is in preview. Learn more about product launch stages.
Take the next step
Start building on Google Cloud with $300 in free credits and 20+ always free products.
Need help getting started?
Contact salesWork with a trusted partner
Find a partnerContinue browsing
See all products