Overview
June 28, 2021
This lesson, from our Cyber Intelligence Foundations course, introduces students to the MITRE ATT&CK framework, and how it can be leveraged to connect malware analysis to the "big picture" of organizational cybersecurity.
Description
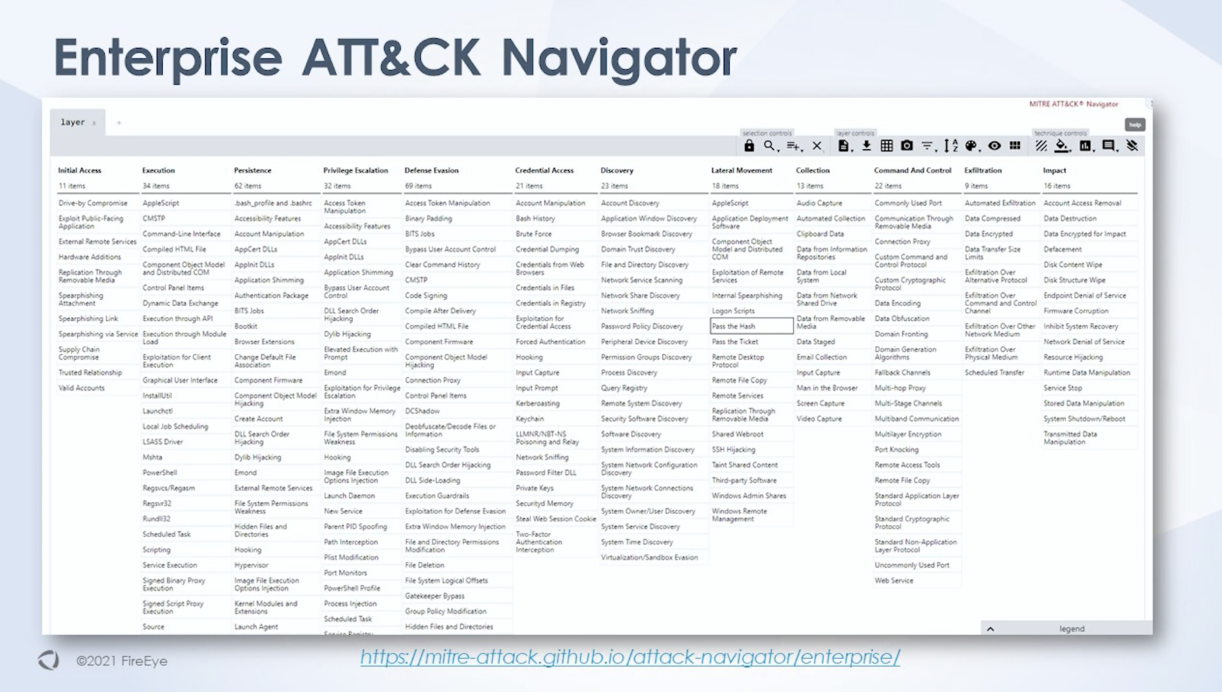
The MITRE ATT&CK framework categorizes cyber threat actor behavior, aiding organizations in understanding their threat profile and risk areas in a structured manner.
The framework organizes adversary goals, such as gaining initial access and escalating privileges, into categories.
Techniques used by adversaries to achieve specific goals are listed under each category.
You can use the framework to research a specific group's tactics, techniques, and procedures (TTPs) and proactively defend against them.
Watch to explore the MITRE ATT&CK framework and gain a deeper understanding of cyber threat actor behaviors and enhance your organization's proactive defense strategies.
Google Threat Intelligence news and alerts
Sign up to receive news and alerts from Google Threat Intelligence