VMs protegidas
Máquinas virtuais com proteção aumentada no Google Cloud.
A VM protegida oferece uma integridade verificável das suas instâncias de VM do Compute Engine. Dessa forma, você tem a garantia de que elas não foram comprometidas por malwares no nível do kernel ou da inicialização.
Recursos
Proteja suas VMs contra ameaças avançadas
Com poucos cliques, é possível ativar as VMs protegidas para ajudar na proteção contra ameaças, como pessoas mal-intencionadas com informações privilegiadas sobre o projeto, firmware convidado malicioso e vulnerabilidades no modo kernel ou de usuário.
Garanta cargas de trabalho confiáveis e verificáveis
Com recursos de inicialização segura e medida, as VMs protegidas ajudam na defesa das máquinas virtuais contra rootkits e malware no nível do kernel e da inicialização. Usando um vTPM, as VMs protegidas oferecem uma raiz de confiança virtual para verificar a identidade das VMs e garantir que elas façam parte da região e do projeto especificados.
Ajude a proteger informações sigilosas contra exportação e reprodução
Usando VMs protegidas, as informações sigilosas geradas ou protegidas por um vTPM são bloqueadas para uma VM e reveladas apenas depois que a integridade é verificada.
Integridade verificável com inicialização segura e medida
A inicialização segura ajuda a impedir o carregamento de códigos nocivos no início da sequência de inicialização. A inicialização medida garante a integridade do carregador de inicialização e dos drivers de kernel e inicialização para proteger a VM contra modificações nocivas.
Resistência à exportação de vTPM
Valide a integridade de pré-inicialização e inicialização de VMs convidadas usando tecnologia vTPM, compatível com especificações do Trusted Computing Group TPM 2.0 e verificada pelo FIPS 140-2 L1. Um vTPM gera e armazena de maneira segura chaves de criptografia ou dados confidenciais em sistemas operacionais convidados.
Firmware UEFI confiável
O firmware confiável é baseado na Unified Extensible Firmware Interface (UEFI) versão 2.3.1, que substitui os subsistemas BIOS legados e ativa o recurso de Inicialização segura da UEFI (em inglês).
Atestados invioláveis
Consiga insights sobre o estado de integridade das VMs protegidas com declarações de atestados invioláveis disponíveis no Cloud Logging e no Cloud Monitoring. Essas medições de integridade ajudam a identificar alterações na referência íntegra da sua VM e no estado atual do ambiente de execução.
Migrações e patches em tempo real
Mantenha as instâncias da máquina virtual em execução mesmo quando ocorrer um evento no sistema host, como atualização de software ou hardware.
Definição de políticas e permissões de IAM
Defina políticas e permissões que obriguem todas as novas instâncias do Compute Engine a usarem imagens de disco de VMs protegidas com as opções de vTPM e monitoramento de integridade ativadas.
Proteção de imagens das VM atuais
Transforme as VMs atuais em VMs protegidas que possam ser executadas no Google Cloud, garantindo integridade verificável e resistência à exfiltração nas imagens atuais.
Como funciona
As VMs protegidas são máquinas virtuais com mais proteção por um conjunto de controles de segurança que ajudam na defesa contra rootkits e bootkits. Essas VMs usam recursos avançados de segurança da plataforma, como inicialização segura e medida, um módulo de plataforma confiável virtual (vTPM, na sigla em inglês), firmware UEFI e monitoramento de integridade.
As VMs protegidas são máquinas virtuais com mais proteção por um conjunto de controles de segurança que ajudam na defesa contra rootkits e bootkits. Essas VMs usam recursos avançados de segurança da plataforma, como inicialização segura e medida, um módulo de plataforma confiável virtual (vTPM, na sigla em inglês), firmware UEFI e monitoramento de integridade.
Usos comuns
Proteger suas VMs
Segurança reforçada para VMs
Segurança reforçada para VMs
Primeiros passos
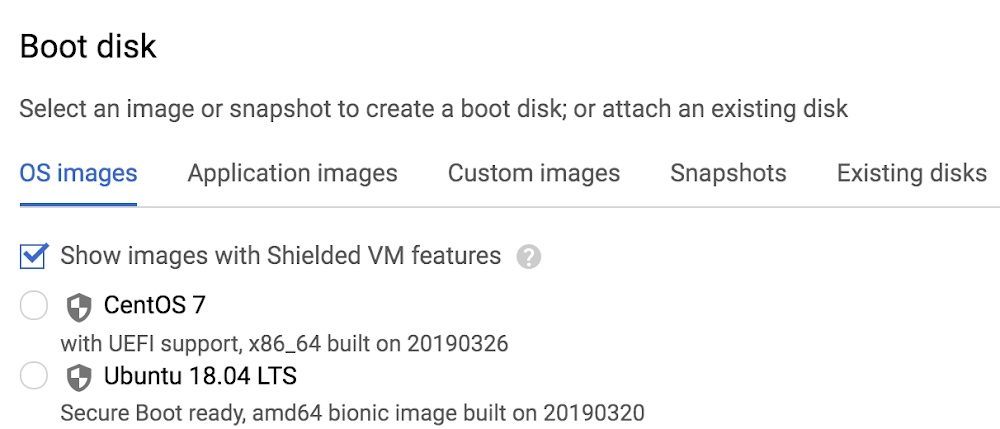
É fácil começar a usar a VM protegida. No console do Google Cloud, ao criar uma nova instância de VM ou modelo de instância, marque a opção "Mostrar imagens com recursos de VM protegida". caixa de seleção.
Agora é possível ajustar as opções de configuração da VM protegida na guia "Segurança". Aqui é possível ter um controle mais granular sobre a funcionalidade da VM protegida, incluindo a opção de ativar ou desativar a Inicialização segura, o vTPM e o monitoramento de integridade. Por padrão, o vTPM e o monitoramento de integridade estão ativados. A Inicialização segura exige ativação explícita.
Se você quiser ter mais controle centralizado e programático sobre as instâncias de VM da sua organização, disponibilizamos uma nova política da organização para VMs protegidas.
Tutoriais, guias de início rápido e laboratórios
Segurança reforçada para VMs
Segurança reforçada para VMs
Primeiros passos
É fácil começar a usar a VM protegida. No console do Google Cloud, ao criar uma nova instância de VM ou modelo de instância, marque a opção "Mostrar imagens com recursos de VM protegida". caixa de seleção.
Agora é possível ajustar as opções de configuração da VM protegida na guia "Segurança". Aqui é possível ter um controle mais granular sobre a funcionalidade da VM protegida, incluindo a opção de ativar ou desativar a Inicialização segura, o vTPM e o monitoramento de integridade. Por padrão, o vTPM e o monitoramento de integridade estão ativados. A Inicialização segura exige ativação explícita.
Se você quiser ter mais controle centralizado e programático sobre as instâncias de VM da sua organização, disponibilizamos uma nova política da organização para VMs protegidas.
Preços
| Preços das VMs protegidas | Não há cobrança adicional pelo uso de VMs protegidas. | |
|---|---|---|
| Serviço | Descrição | Preços |
VMs protegidas | Ative as opções de VM protegida no console do Google Cloud. | Grátis |
Preços das VMs protegidas
Não há cobrança adicional pelo uso de VMs protegidas.
VMs protegidas
Ative as opções de VM protegida no console do Google Cloud.
Grátis