Google Security Operations - Detect
Detect more threats with less effort
Ingest all your data with twelve months hot data retention and eliminate blind spots with modern threat detection powered by Google.
Learn more about the Google Security Operations platform.
Features
Uncover more threats with less custom engineering
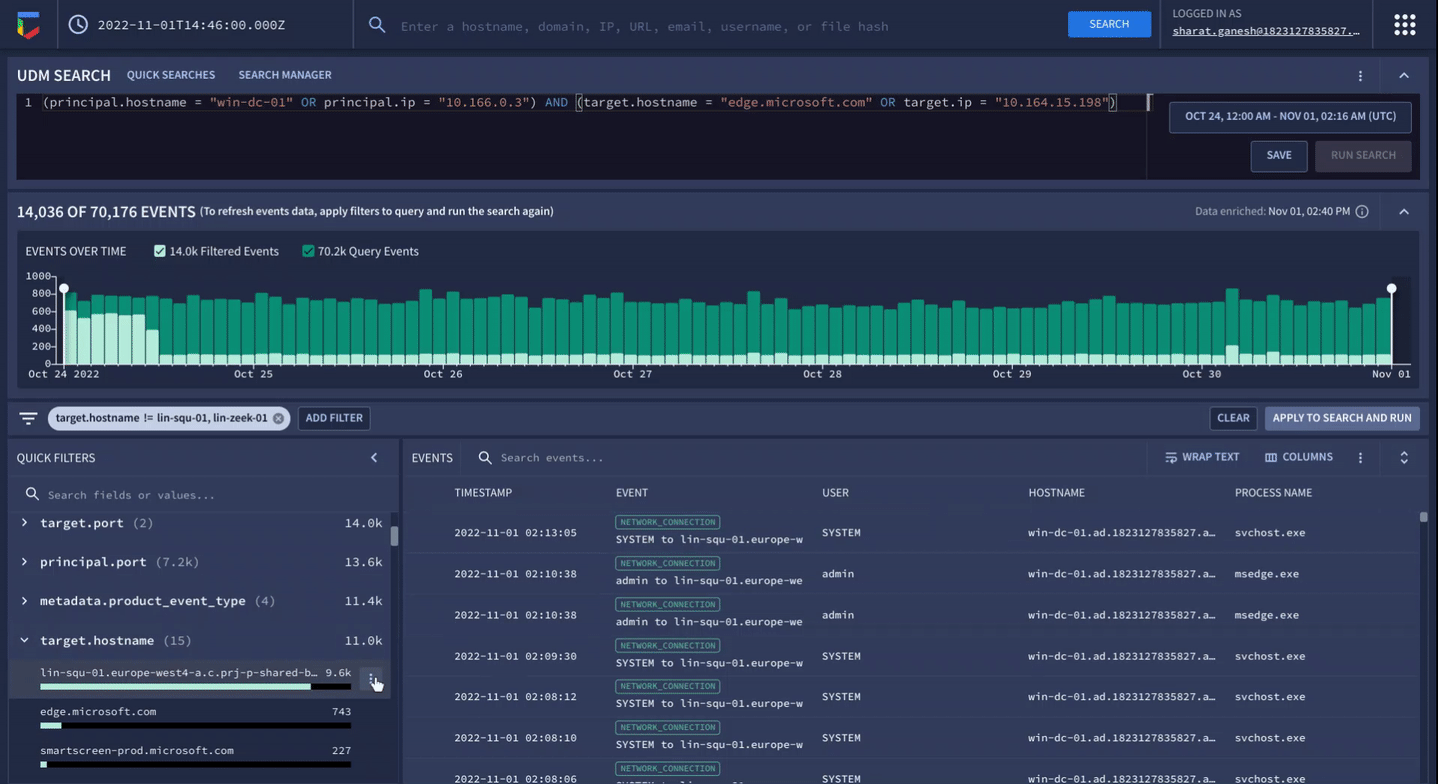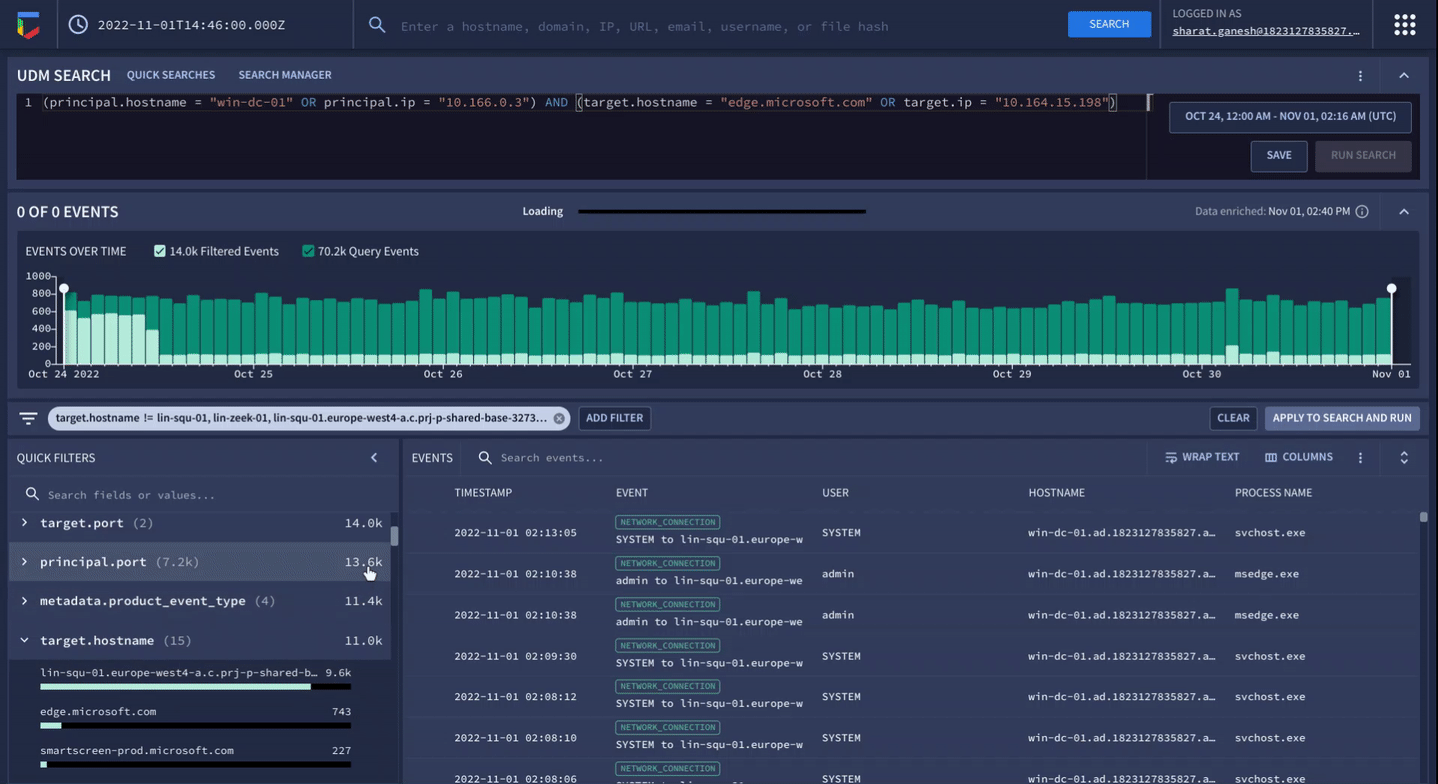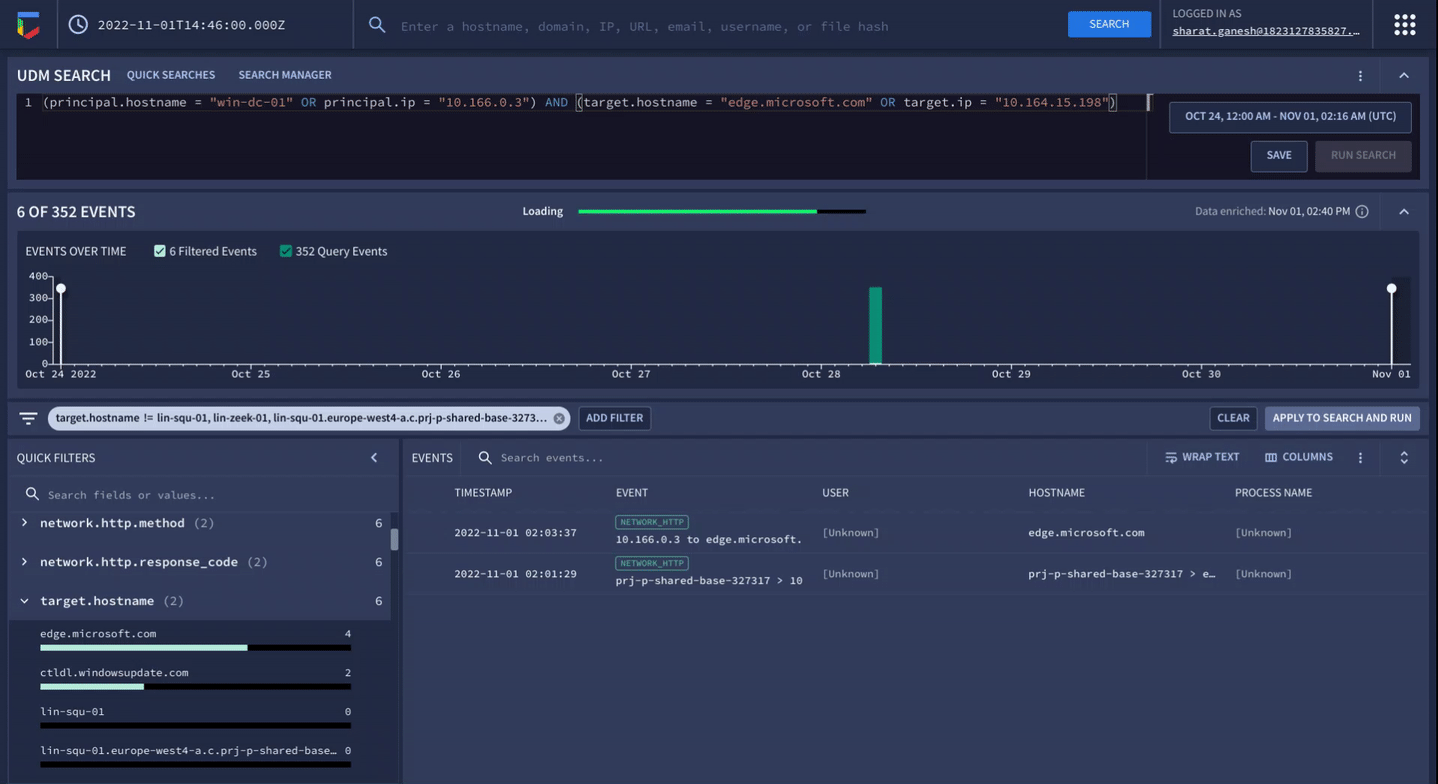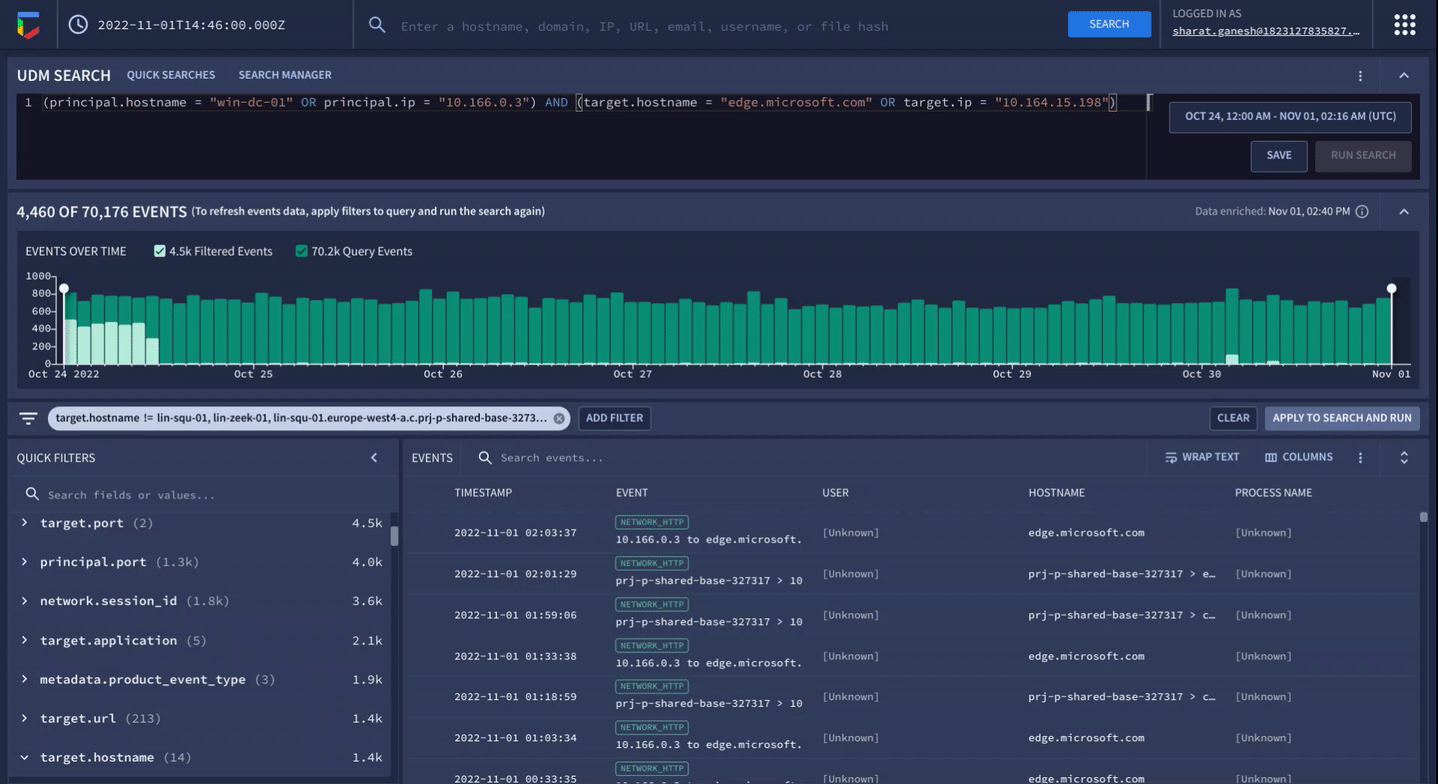
Correlate petabytes of your telemetry and get actionable threat information with sub-second search.
Leverage Google curated detections to find the latest threats and map them to MITRE ATT&CK.
Use natural language to search your data, iterate, and drill down. Gemini generates underlying queries and presents fully mapped syntax.
Create detections with context-aware AI-powered chat.
Only escalate important threats with risk scoring based on contextual vulnerability and business risk.
Easily build YARA-L detections to create rules for your own environment, including user and entity behavior analytics.
Proactively uncover and defend against the latest threats
Automatically surface and prioritize findings with access to rich context about threat actors and campaigns from applied threat intelligence.
Leverage intelligence from Google, Mandiant, and VirusTotal to automatically uncover potential threats.
Get early warning signals of potential active breaches in your environment based on Mandiant’s frontline intelligence from real-world incident response investigations.
Identify potentially exploitable entry points accessible to attackers and prioritize remediation with attack surface management integration.
Eliminate blind spots using the power of the cloud
Ingest and analyze data at scale leveraging Google Cloud’s planetary scale to quickly and securely ingest all relevant security telemetry at a predictable price point.
Continuously analyze twelve months of hot data by default to enable retroactive matching of IoCs and threat hunting by your team or by Mandiant experts.
Detect more threats with ease using built in integrations with your Google Cloud infrastructure as well as multi-cloud and on-prem.
How It Works
Google Security Operations offers a unified experience across SIEM, SOAR, and threat intelligence to drive better detection, investigation, and response. Collect security telemetry data, apply threat intel to identify high priority threats, drive response with playbook automation, case management, and collaboration.
Google Security Operations offers a unified experience across SIEM, SOAR, and threat intelligence to drive better detection, investigation, and response. Collect security telemetry data, apply threat intel to identify high priority threats, drive response with playbook automation, case management, and collaboration.
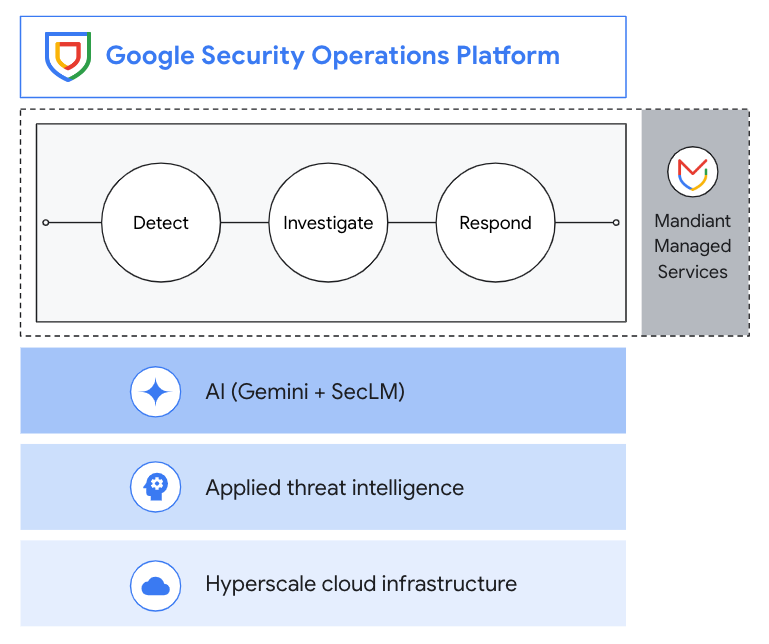
Common Uses
Threat detection
Investigation
Hunting
Pricing
| About Google Security Operations pricing | Google Security Operations is available in packages and based on ingestion. Includes one year of security telemetry retention at no additional cost. | |
|---|---|---|
| Product | Description | Pricing |
Standard | Base SIEM and SOAR capabilities Includes the core capabilities for data ingestion, threat detection, investigation and response with 12 months hot data retention, full access to our 800+ parsers and 300+ SOAR integrations and 1 environment with remote agent. The detection engine for this package supports up to 1,000 single-event and 75 multi-event rules. Choose a subset of Curated Detection rules. Threat intelligence Bring your own threat intelligence feeds. Data pipeline management Includes limited filtering and transforms. | Contact sales for pricing |
Enterprise | Includes everything in the Standard package plus: Base SIEM and SOAR capabilities Expanded support to unlimited environments with remote agent and a detection engine that supports up to 2,000 single-event and 125 multi-event rules. UEBA Use YARA-L to create rules for your own user and entity behavior analytics, plus get a risk dashboard and out of the box user and entity behavior-style detections. Threat intelligence Adds curation of enriched open source intelligence that can be used for filtering, detections, investigation context and retro-hunts. Enriched open source intelligence includes Google Safe Browsing, remote access, Benign, and OSINT Threat Associations. Google curated detections Access out-of-the-box detections maintained by Google experts, covering on-prem and cloud threats. Gemini in security operations Take productivity to the next level with AI. Gemini in security operations provides natural language, an interactive investigation assistant, contextualized summaries, recommended response actions and detection, and playbook creation. Data pipeline management Includes limited filtering and transforms. | Contact sales for pricing |
Enterprise Plus | Includes everything in the Enterprise package plus: Base SIEM and SOAR capabilities Expanded detection engine supporting up to 3,500 single-event rules and 200 multi-event rules. Applied threat intelligence Full access to Google Threat Intelligence (which includes Mandiant, VirusTotal, and Google threat intel), including intelligence gathered from active Mandiant incident response engagements. On top of the unique sources, Applied Threat Intelligence provides turnkey prioritization of IoC matches with ML-base prioritization that factors in each customer's unique environment. We will also go beyond IoCs to include TTPs in understanding how an adversary behaves and operates. Google curated detections Additional access to emerging threat detections based on Mandiant's primary research and frontline threats seen in active incident response engagements. Data pipeline management Includes advanced filtering, redaction, transformations, and routing to Google. Additionally, 12 months of routing to other destinations for SIEM migrations is included. BigQuery UDM storage Free storage for BigQuery exports for Google SecOps data up to your retention period (12 months by default). | Contact sales for pricing |
About Google Security Operations pricing
Google Security Operations is available in packages and based on ingestion. Includes one year of security telemetry retention at no additional cost.
Standard
Base SIEM and SOAR capabilities
Includes the core capabilities for data ingestion, threat detection, investigation and response with 12 months hot data retention, full access to our 800+ parsers and 300+ SOAR integrations and 1 environment with remote agent.
The detection engine for this package supports up to 1,000 single-event and 75 multi-event rules. Choose a subset of Curated Detection rules.
Threat intelligence
Bring your own threat intelligence feeds.
Data pipeline management
Includes limited filtering and transforms.
Contact sales for pricing
Enterprise
Includes everything in the Standard package plus:
Base SIEM and SOAR capabilities
Expanded support to unlimited environments with remote agent and a detection engine that supports up to 2,000 single-event and 125 multi-event rules.
UEBA
Use YARA-L to create rules for your own user and entity behavior analytics, plus get a risk dashboard and out of the box user and entity behavior-style detections.
Threat intelligence
Adds curation of enriched open source intelligence that can be used for filtering, detections, investigation context and retro-hunts. Enriched open source intelligence includes Google Safe Browsing, remote access, Benign, and OSINT Threat Associations.
Google curated detections
Access out-of-the-box detections maintained by Google experts, covering on-prem and cloud threats.
Gemini in security operations
Take productivity to the next level with AI. Gemini in security operations provides natural language, an interactive investigation assistant, contextualized summaries, recommended response actions and detection, and playbook creation.
Data pipeline management
Includes limited filtering and transforms.
Contact sales for pricing
Enterprise Plus
Includes everything in the Enterprise package plus:
Base SIEM and SOAR capabilities
Expanded detection engine supporting up to 3,500 single-event rules and 200 multi-event rules.
Applied threat intelligence
Full access to Google Threat Intelligence (which includes Mandiant, VirusTotal, and Google threat intel), including intelligence gathered from active Mandiant incident response engagements.
On top of the unique sources, Applied Threat Intelligence provides turnkey prioritization of IoC matches with ML-base prioritization that factors in each customer's unique environment. We will also go beyond IoCs to include TTPs in understanding how an adversary behaves and operates.
Google curated detections
Additional access to emerging threat detections based on Mandiant's primary research and frontline threats seen in active incident response engagements.
Data pipeline management
Includes advanced filtering, redaction, transformations, and routing to Google. Additionally, 12 months of routing to other destinations for SIEM migrations is included.
BigQuery UDM storage
Free storage for BigQuery exports for Google SecOps data up to your retention period (12 months by default).
Contact sales for pricing
Learn what Google Security Operations can do for you
Business Case
Explore how organizations like yours cut costs, increase ROI, and drive innovation with Google Security Operations
Forrester Consulting Study: Customers cite 240% ROI with Google Security Operations
CISO, Insurance company
"In simple terms, Google SecOps is a mass risk-reducer. Threats that would have impacted our business no longer do, because we have greater observability, better mean time to detect, and better mean time to respond."
Related content
Trusted and loved by security teams around the world
"The Gemini AI functionality within Google Security Operations really impressed me. It gives you essentially 70 or 80 percent of the detection right out of the box and then you only have to add those kinds of small things in the middle."- Manan Doshi, Senior Security Engineer, Etsy
"With the traditional SIEM, it would typically take five to seven people with an environment our size. With Google Security Operations, we’re logging approximately 22 times the amount of data, we're seeing three times the events, and we're closing investigations in half the time."- Mike Orosz, CISO, Vertiv
"Historically, our legacy SIEM, we had to feed it a lot of the contextual enrichment and all of that threat intelligence stuff. It was data engineering to make it sing, where on the Google side, the product is more baked in, purpose-built for us to use it. It’s so intuitive and the speed was certainly really beneficial for us as well."- Mark Ruiz, Head of Cybersecurity Analytics, Pfizer