Mandiant Threat Intelligence
Know who's targeting you
Get visibility into the latest threats with cyber threat intelligence directly from the frontlines.
Features
Threat intel informed by open source and frontline experiences
Mandiant Threat Intelligence is the product of 200k+ hours per year spent responding to cyber attacks and open source threat intel (OSINT). All of this is curated by our 500+ threat intel analysts from over 30 countries who turn this information into human and machine-readable intelligence to help you better understand your threat landscape.
Source: Google Internal Data, December, 2023
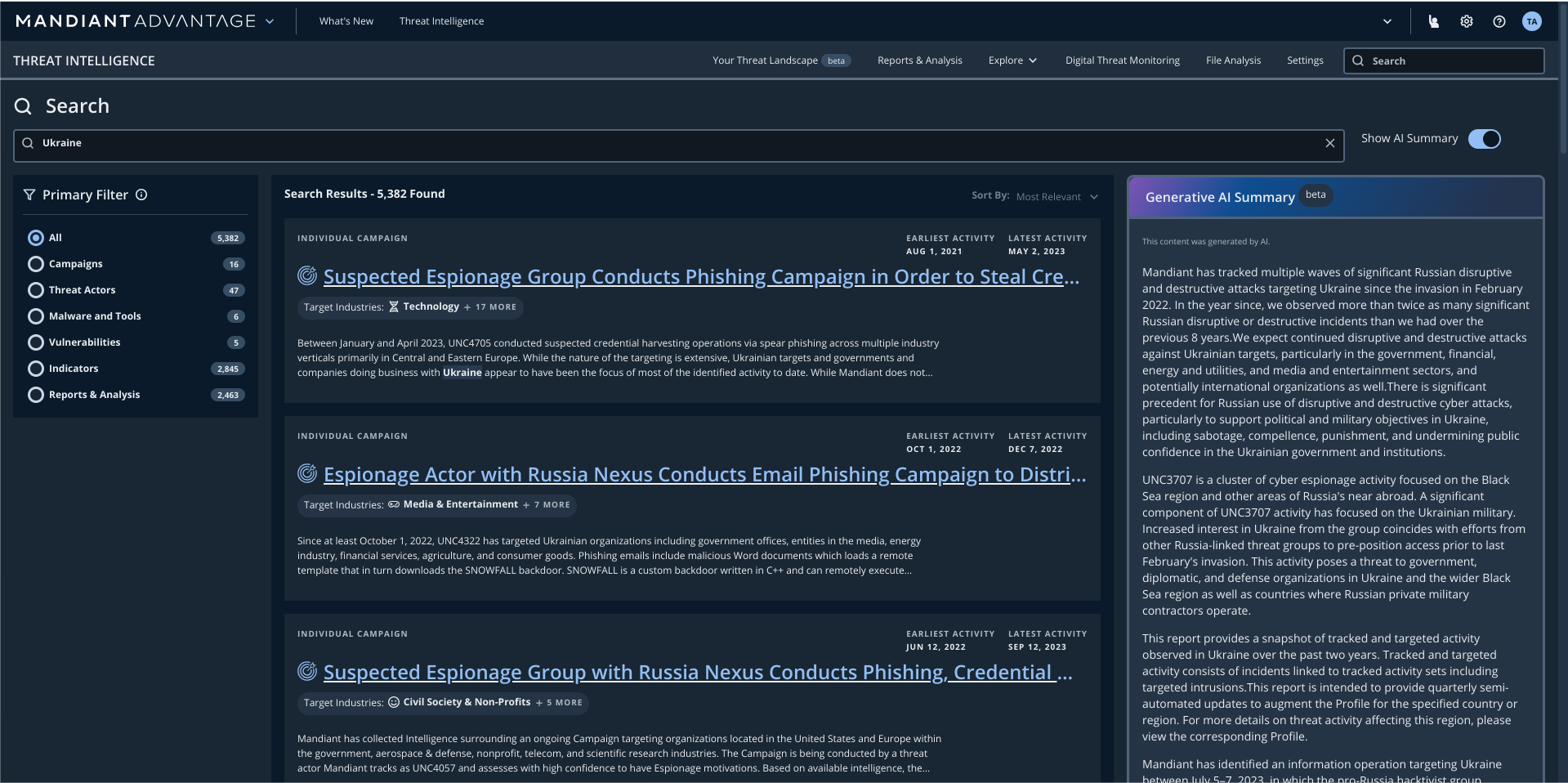
AI-powered search summaries
Leverage Gemini in Threat Intelligence, an always on AI collaborator that provides generative AI-powered assistance in simplifying complex threat intel into easily digestible summaries, so your organization can make informed decisions to help reduce risk faster and more effectively when faced with limited time and resources.
Mandiant Intelligence Expertise
Optimize your ability to consume, analyze, and apply threat intelligence. Leverage Mandiant’s expertise to deliver threat intelligence tailored to your organization in the way you need it.
Cyber Threat Profile assessment
Leverage Mandiant’s expertise with a Cyber Threat Profile assessment. This service will develop a composite picture of the most relevant cyber threats to your organization. You will learn how those threats can materialize to impact you and your partners, now and in the future. A Cyber Threat Profile will help you shape your intelligence-led security strategy and reduce communication gaps between departments.
Threat insights within your existing workflows
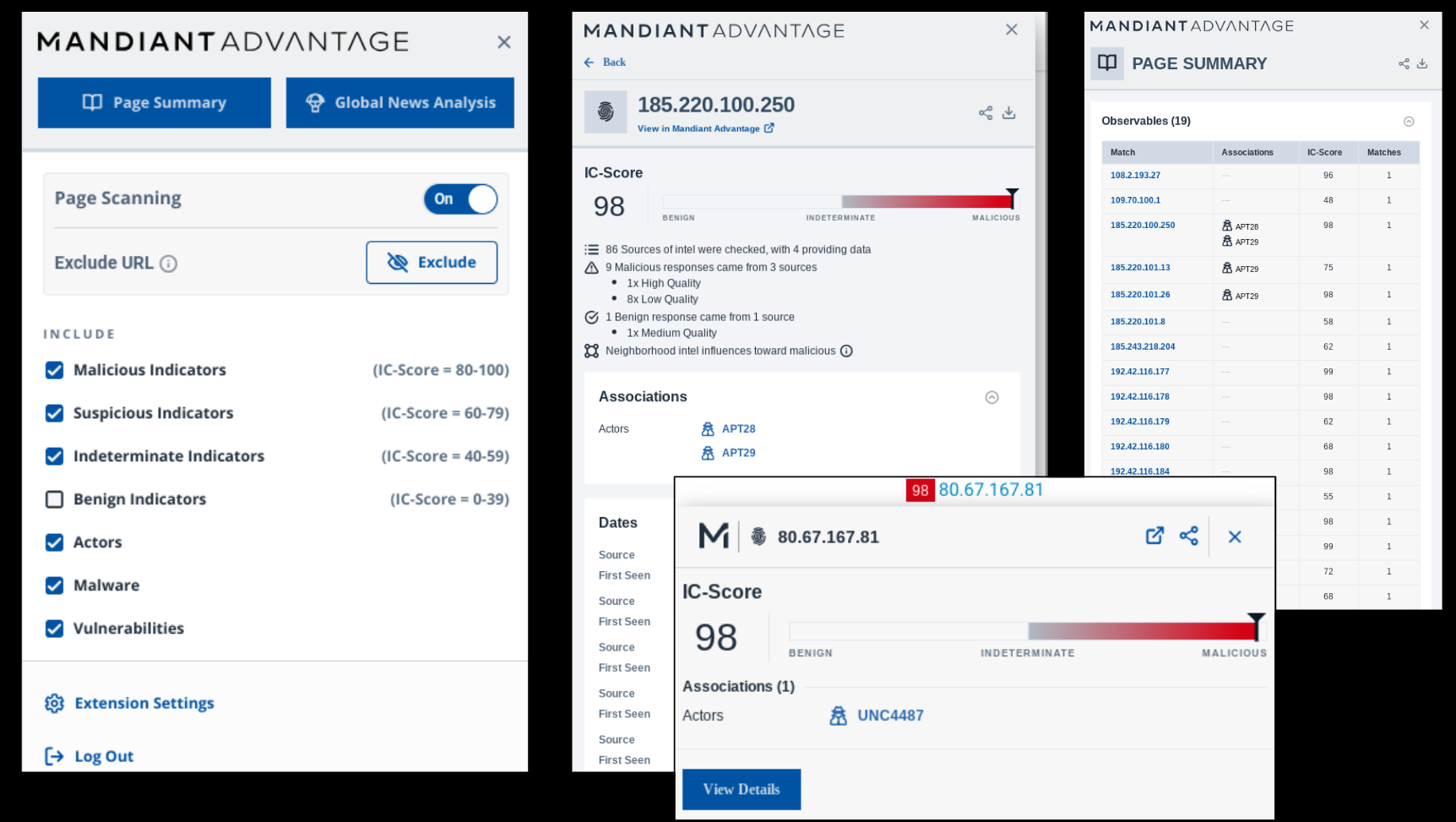
Embed and overlay the most recent threat insights into any web page or security analytics tool, including SIEMs, NTAs, and EDRs, with Mandiant’s browser plug-in or API. Reduce the need to pivot between multiple tools by viewing news analysis, indicator scoring, and threat context as they appear on the page or click the links to access further detail.
Expert insights and context
Search for threat indicators by IP, URL, domain, and file hash to get expert-based indicator confidence score (IC-Score), timing, and actor context. Navigate quickly between actors, malware, tactics, and vulnerability reports to get a 360-degree view of ongoing threat activity, plus receive daily news analysis with insights from Mandiant specialists to determine which news sources to trust and why.
How It Works
Mandiant Threat Intelligence can help security teams set or adjust their security strategy by providing detailed intelligence on the most relevant malware, vulnerabilities, and the adversaries targeting them, including the tactics, techniques, and procedures used in an attack.
Mandiant Threat Intelligence can help security teams set or adjust their security strategy by providing detailed intelligence on the most relevant malware, vulnerabilities, and the adversaries targeting them, including the tactics, techniques, and procedures used in an attack.
Common Uses
Learn faster with AI-generated summaries
Leverage the power of Gemini in Threat Intelligence
Save time and reduce complexity when researching threats or geopolitical topics. Use Gemini in Threat Intel, an always on AI collaborator that provides generative AI-powered assistance to help distill Mandiant’s industry-leading corpus of threat intel into easy-to-comprehend summaries, which help you quickly understand how adversaries may be targeting your org and impacting the threat landscape.
Learning resources
Leverage the power of Gemini in Threat Intelligence
Save time and reduce complexity when researching threats or geopolitical topics. Use Gemini in Threat Intel, an always on AI collaborator that provides generative AI-powered assistance to help distill Mandiant’s industry-leading corpus of threat intel into easy-to-comprehend summaries, which help you quickly understand how adversaries may be targeting your org and impacting the threat landscape.
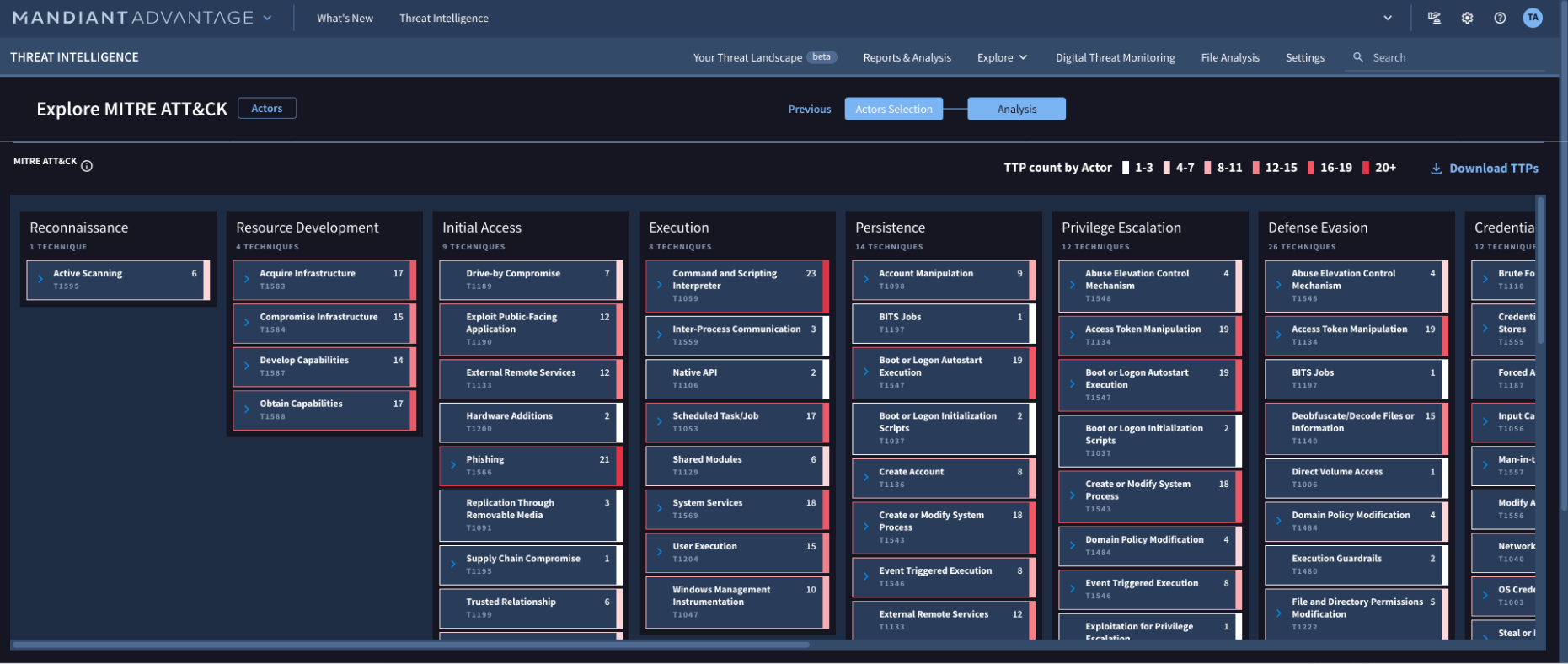
Visibility into threat actor playbooks
Know how the attack will happen before it starts
Set a proactive security strategy by mapping the tactics, techniques, and procedures (TTPs) used against organizations just like yours. By mapping the TTPs with the MITRE ATT&CK framework you will be able to prioritize tasks, make adjustments to security settings, and make security investments with more confidence.
Learning resources
Know how the attack will happen before it starts
Set a proactive security strategy by mapping the tactics, techniques, and procedures (TTPs) used against organizations just like yours. By mapping the TTPs with the MITRE ATT&CK framework you will be able to prioritize tasks, make adjustments to security settings, and make security investments with more confidence.
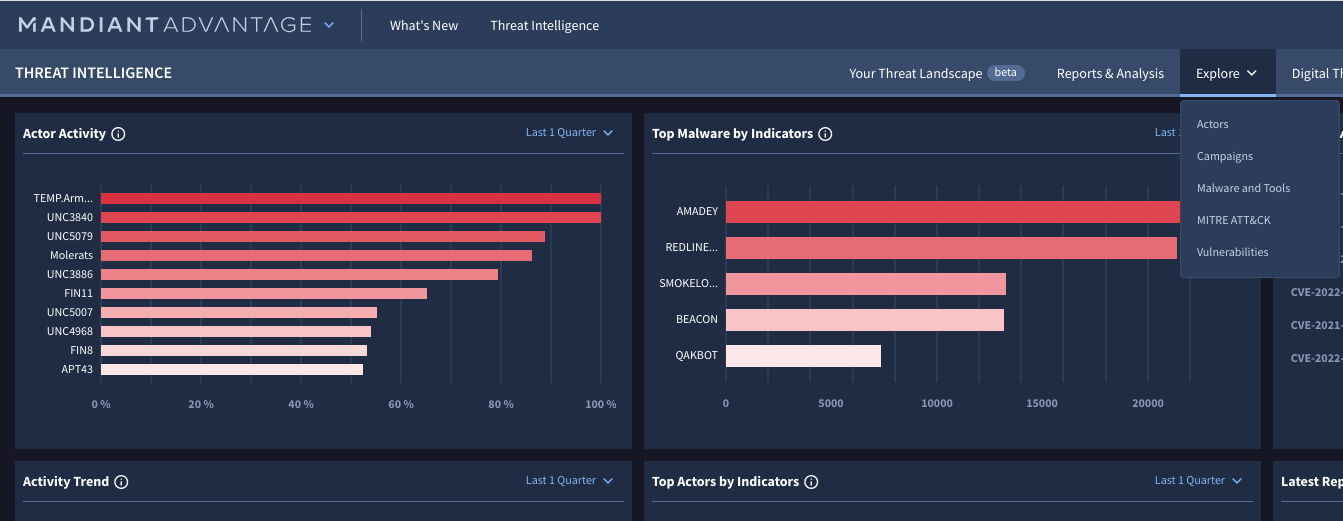
Better understand your threat landscape
Receive to-the-minute intelligence with analysis
Gathering threat intelligence shouldn’t be an arduous task of searching the web for credible intelligence. Mandiant’s unique data intelligence gathering, research, curation, and dissemination enable organizations to attribute threat actors quickly. This helps reduce your time spent researching and allows you to be more proactive with your security settings.
Learning resources
Receive to-the-minute intelligence with analysis
Gathering threat intelligence shouldn’t be an arduous task of searching the web for credible intelligence. Mandiant’s unique data intelligence gathering, research, curation, and dissemination enable organizations to attribute threat actors quickly. This helps reduce your time spent researching and allows you to be more proactive with your security settings.
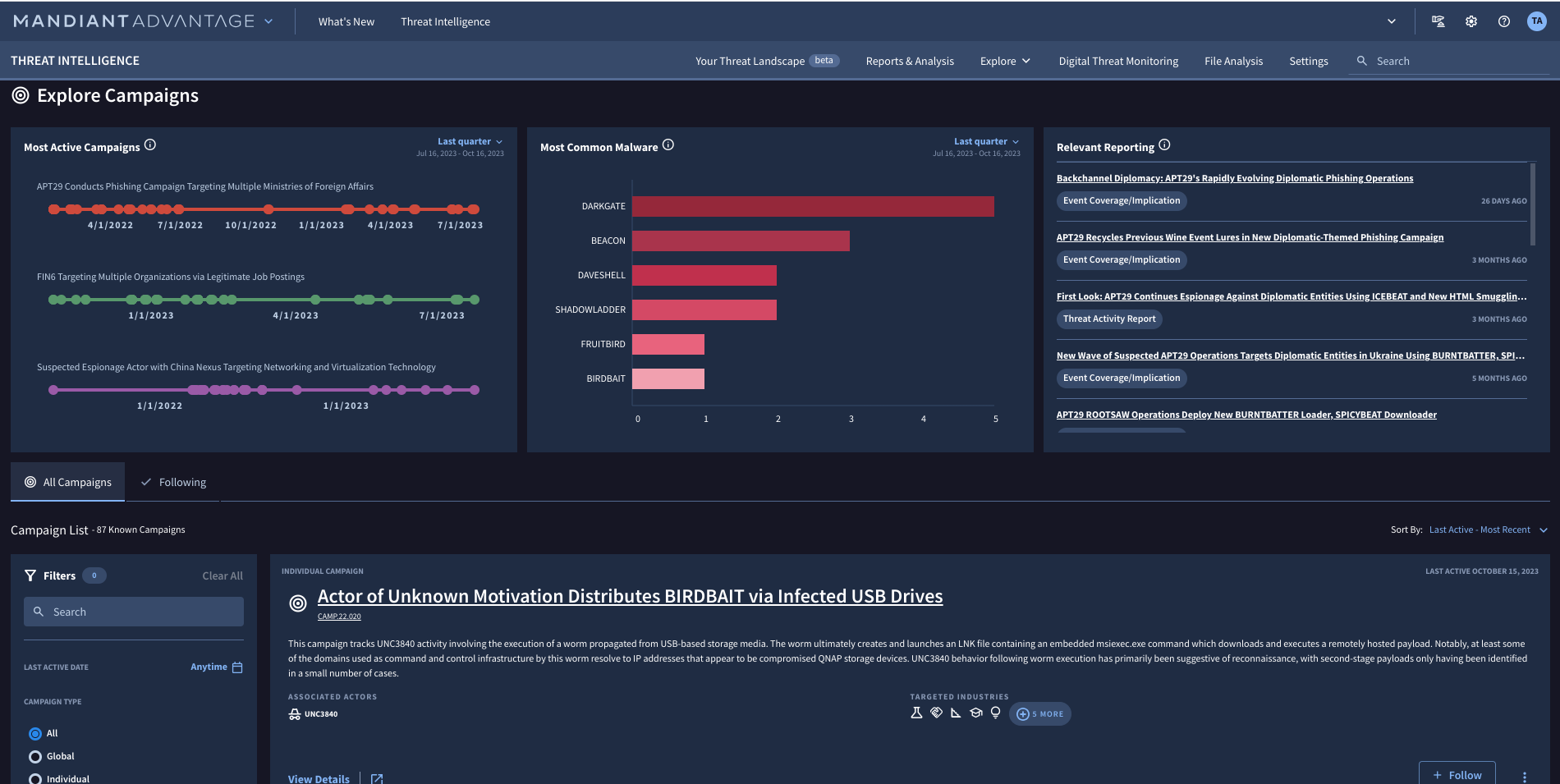
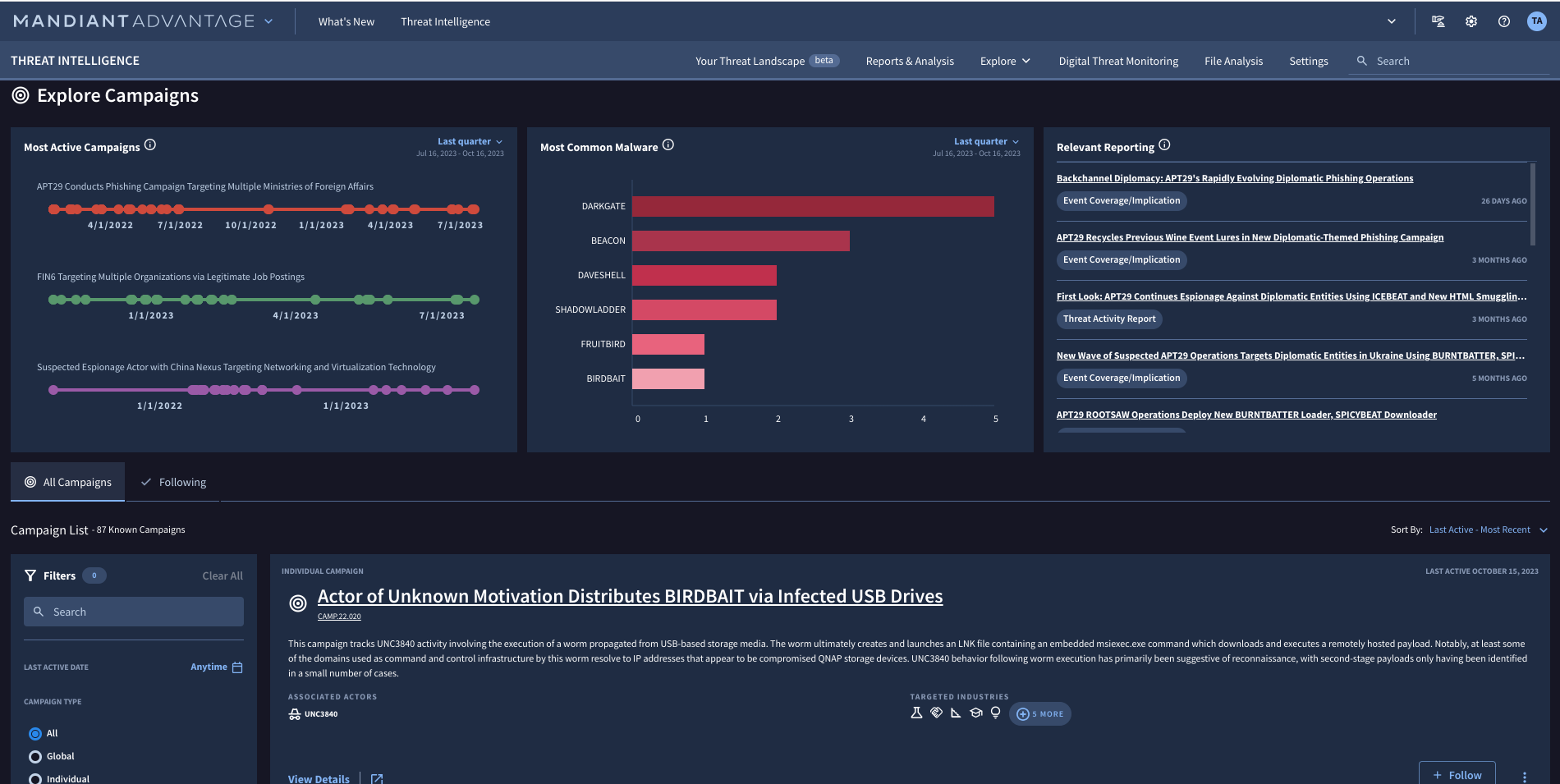
Visibility into active threat campaigns
Anticipate, identify, and respond to threats with confidence
Threat intel can be helpful to proactively set your security strategy, but when you need to know if there are any active threat campaigns targeting your region, industry, or vulnerabilities, Mandiant Threat Intel can help provide actionable insight into these campaigns. With this knowledge you can adjust your strategy quickly, driving better prioritization and mitigation of current and future threats.
Learning resources
Anticipate, identify, and respond to threats with confidence
Threat intel can be helpful to proactively set your security strategy, but when you need to know if there are any active threat campaigns targeting your region, industry, or vulnerabilities, Mandiant Threat Intel can help provide actionable insight into these campaigns. With this knowledge you can adjust your strategy quickly, driving better prioritization and mitigation of current and future threats.
Direct access to Mandiant expertise
Level-up your security team
Optimize your threat intelligence with Mandiant Intelligence Expertise. This collection of services can help you optimize your ability to consume, analyze, and apply threat intelligence. Get expert assistance to help build a sustainable intelligence-led organization and improve your team’s analytical and threat-hunting capabilities.
Learning resources
Level-up your security team
Optimize your threat intelligence with Mandiant Intelligence Expertise. This collection of services can help you optimize your ability to consume, analyze, and apply threat intelligence. Get expert assistance to help build a sustainable intelligence-led organization and improve your team’s analytical and threat-hunting capabilities.
Put threat intel into your workflows
Streamline the operationalization of threat intel
Get actionable intelligence directly in your browser and improve efficiency within your existing workflows. Overlay threat intelligence in your browser to learn more about a vulnerability, indicator, malware, or threat actor without leaving your browser or workflow, including social media sites, SaaS-based security consoles, and more.
Learning resources
Streamline the operationalization of threat intel
Get actionable intelligence directly in your browser and improve efficiency within your existing workflows. Overlay threat intelligence in your browser to learn more about a vulnerability, indicator, malware, or threat actor without leaving your browser or workflow, including social media sites, SaaS-based security consoles, and more.
Pricing
| How Mandiant Threat Intelligence pricing works | Mandiant Threat Intelligence is licensed based on the number of an organization’s employees. Please contact sales for more info on pricing. | |
|---|---|---|
| Threat intelligence | Description | Pricing |
Mandiant Threat Intelligence | Mandiant Threat Intelligence | Mandiant Threat Intelligence has two subscription options: Security Operations and Fusion. Both are licensed based on the number of employees. |
Mandiant Intelligence Expertise | Mandiant Intelligence Expertise services are offered as either perpetual services, which are ideal for organizations that need ongoing access to intelligence and support, or purchased to meet a specific use case. | |
How Mandiant Threat Intelligence pricing works
Mandiant Threat Intelligence is licensed based on the number of an organization’s employees. Please contact sales for more info on pricing.
Mandiant Threat Intelligence
Mandiant Threat Intelligence
Mandiant Threat Intelligence has two subscription options: Security Operations and Fusion. Both are licensed based on the number of employees.
Mandiant Intelligence Expertise
Mandiant Intelligence Expertise services are offered as either perpetual services, which are ideal for organizations that need ongoing access to intelligence and support, or purchased to meet a specific use case.