Overview
This lesson, from the Cyber Intelligence Foundations course, looks closer at how different stakeholders within an organization use intelligence.
Description
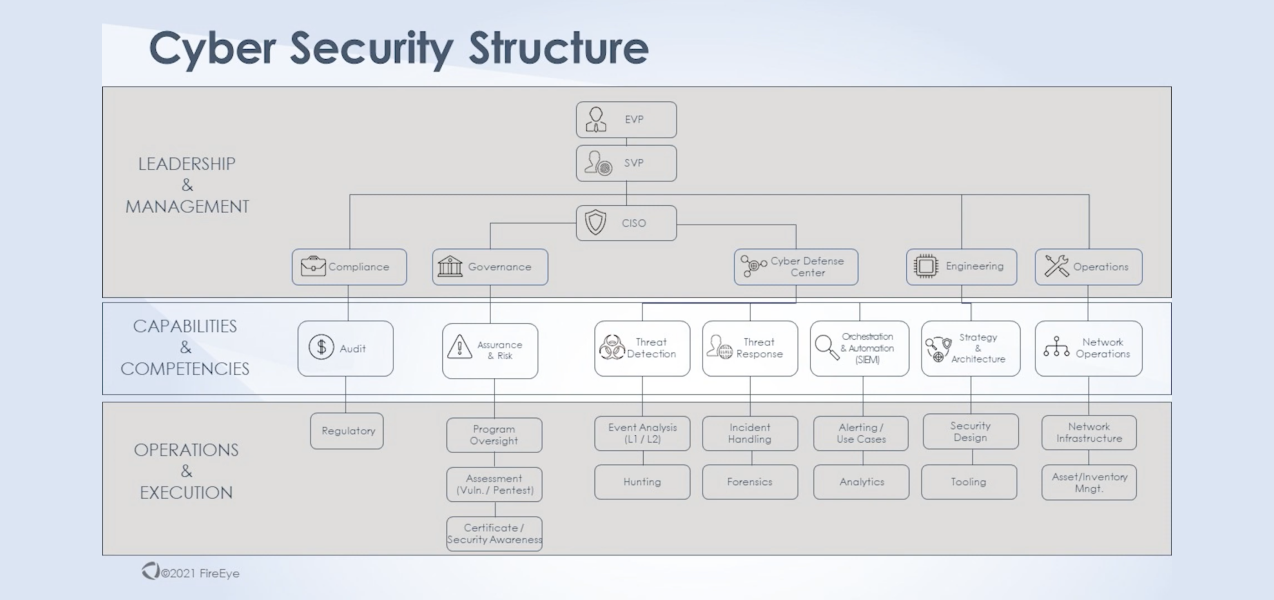
This video discusses how Cyber Threat Intelligence (CTI) can be used within a cybersecurity organization. It highlights the different stakeholders within an organization that should be receiving value from intelligence, including assurance and risk functions, executives, hunt missions, incident responders, and security design teams.
It emphasizes that intelligence must be actionable and include recommendations or a list of items that are already being undertaken to mitigate or resolve threats. It also notes that CTI should be able to integrate with security controls and tools and function at the automation level by using one of the industry standard data formats.
Different types of intelligence serve different functions within the organization:
- Strategic intelligence: Provides a high-level overview of threats and is useful for risk assessments and informing executives about the risks facing their business operations.
- Operational intelligence: Produces content on tactics, techniques, and procedures (TTPs) and is valuable for event analysis and incident response.
- Tactical intelligence: Provides detailed information on specific threats and can be used to prioritize alerts and validate security controls.
Watch to understand the importance of CTI in helping organizations understand and mitigate cyber threats.
Google Threat Intelligence news and alerts
Sign up to receive news and alerts from Google Threat Intelligence