Google Threat Intelligence
Actionable threat intelligence at Google scale
Get comprehensive visibility and context on the threats that matter most to your organization.
Features
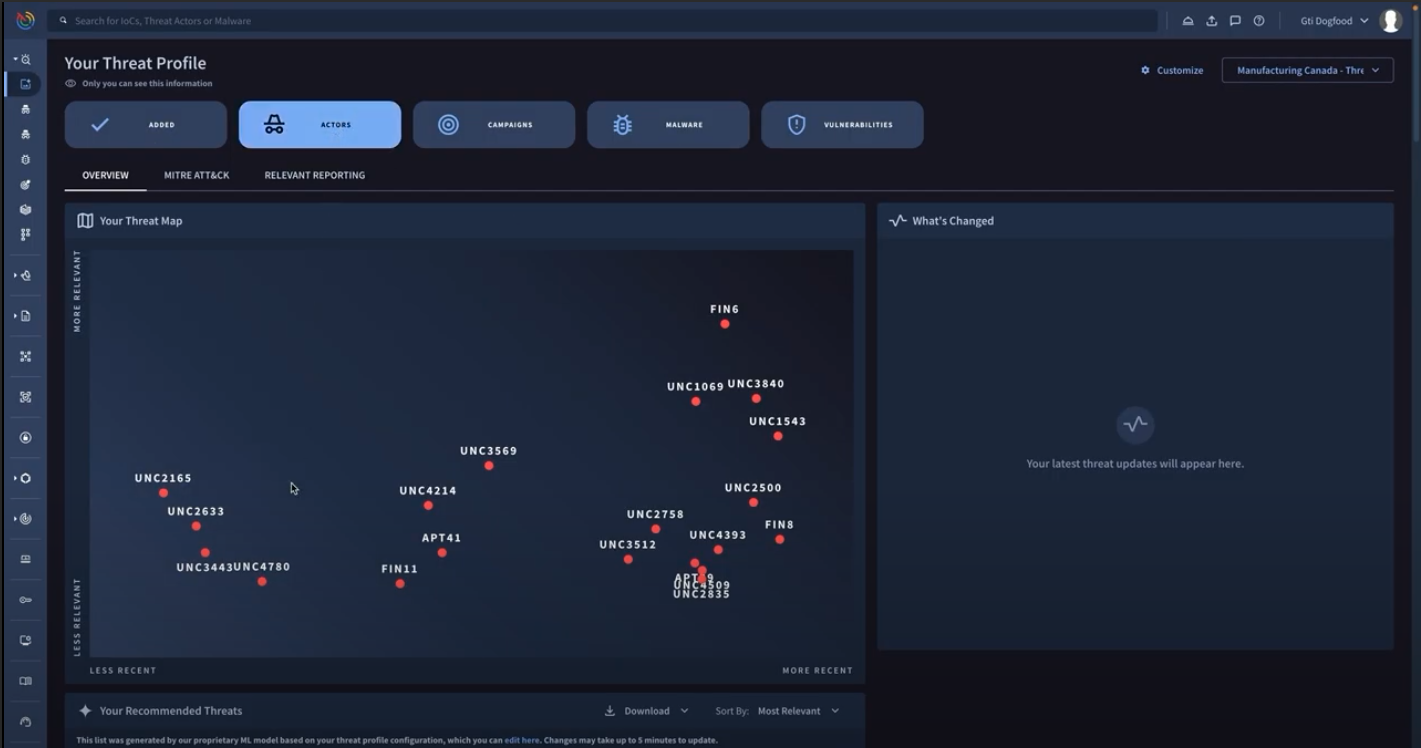
Know who’s targeting you with unmatched visibility
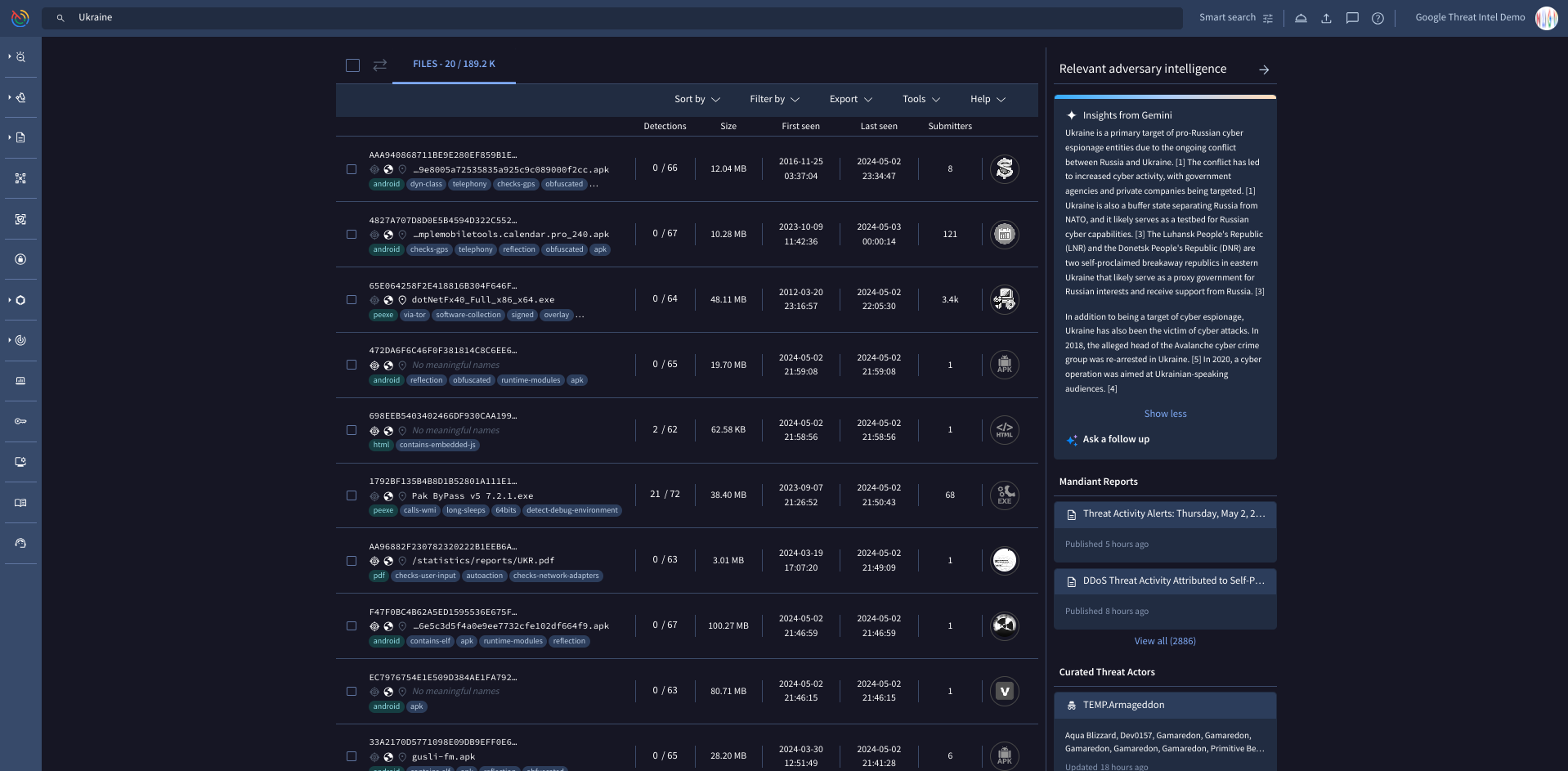
Google Threat Intelligence provides unmatched visibility into threats enabling us to deliver detailed and timely threat intelligence to security teams around the world. By defending billions of users, seeing millions of phishing attacks, and spending hundreds of thousands of hours investigating incidents we have the visibility to see across the threat landscape to keep the most important organizations protected, yours.
Turn insights into action
Focus on the most relevant threats to your organization by understanding the threat actors and their ever changing tactics, techniques, and procedures (TTPs). Leverage these insights to proactively set your defenses, hunt efficiently, and respond to new and novel threats in minutes.
Make Google part of your security team
Grow your team’s capabilities with Mandiant’s industry leading threat analysts. Our threat intel experts are on your side and here to help. Whether you're looking for cyber threat intel (CTI) training for your team, needing a deeper understanding of threats you should prioritize and action, or needing a CTI expert to sit with your team, we have the expertise to help you maximize threat intel.
Get help directly within the console from a Mandiant expert to address threats faster and move to your next task.
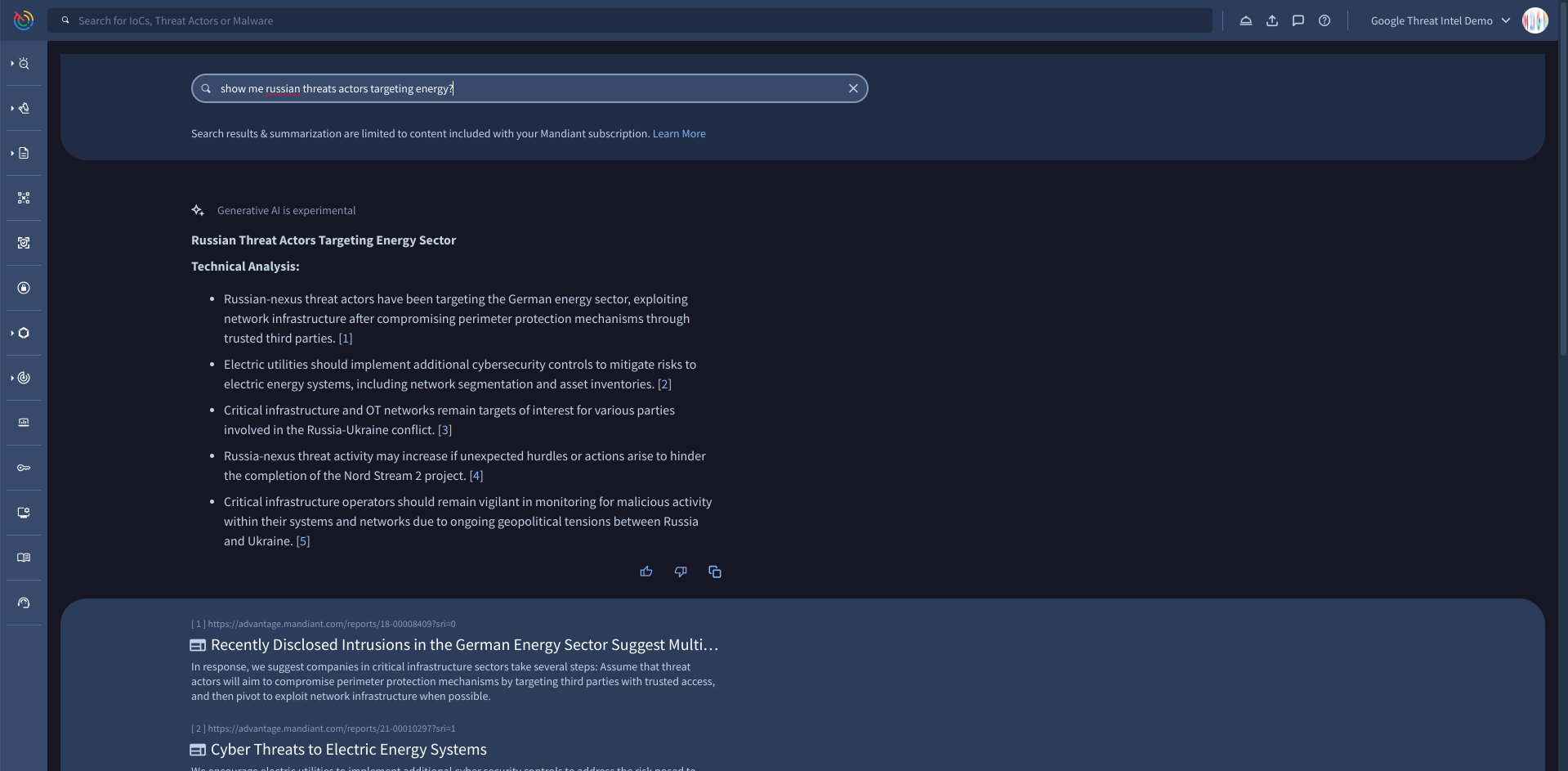
Supercharge your team with Gemini
Optimize your work flows with the help of AI. Gemini in Threat Intelligence analyzes vast datasets and acts as a force multiplier, immediately surfacing threats most relevant to your unique risk profile, reducing the noise of generic alerts. It continuously learns from your actions, tailoring its output to become increasingly relevant to your specific needs over time.
Simplify workflows and collaboration with a workbench
Take command of your threat analysis. Our threat intelligence workbench puts everything you need in one place: a vast malware database, powerful tools, insightful context, and effortless collaboration. Customize workflows with graphs, hunting results, rule sharing, and collections to maximize efficiency.
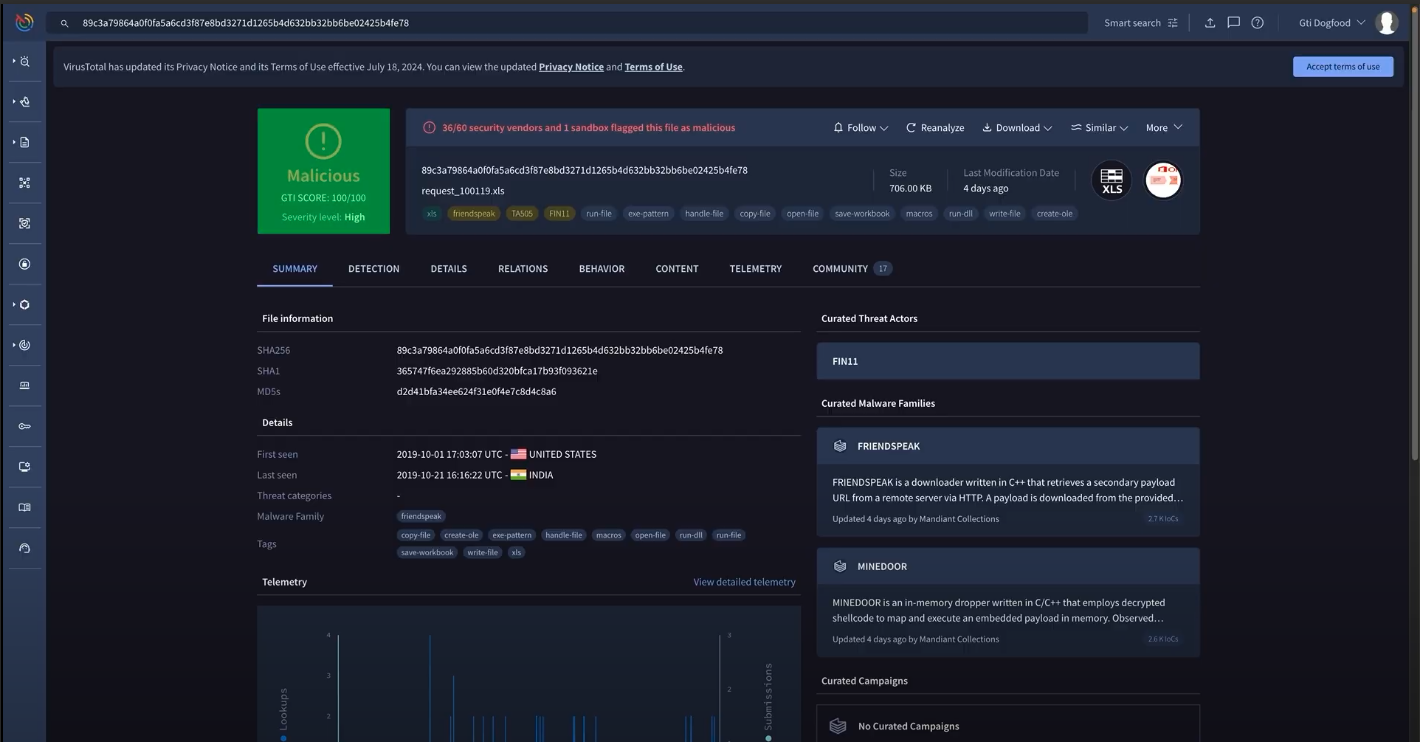
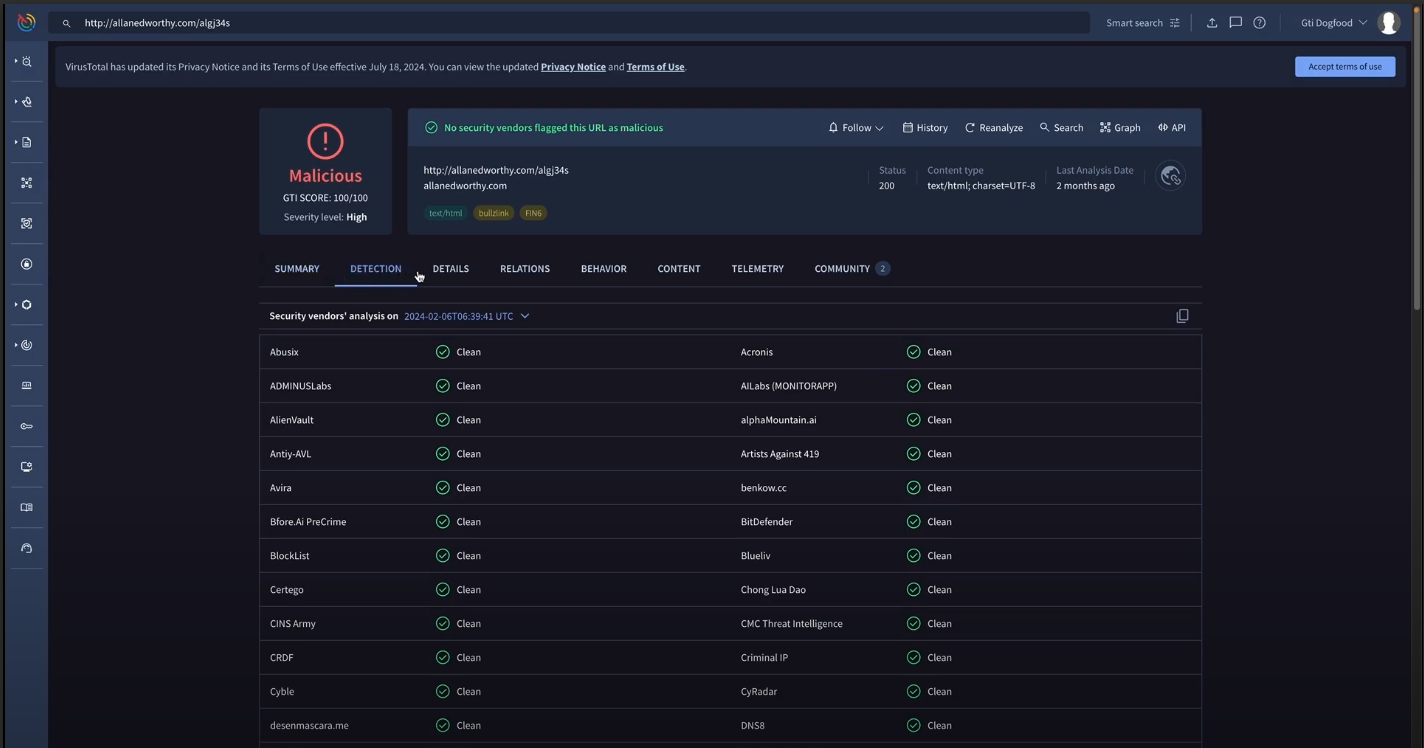
Trust a unified verdict
When it comes to security and the threats you are facing, you need to have confidence in the threat intelligence you use. Google Threat Intelligence pulls together inputs from Google’s vast threat insights, Mandiant’s frontline and human curated threat intelligence, and VirusTotal’s massive threat database to deliver a unified verdict. This provides you with a single answer on whether an indicator or suspicious object is something you should prioritize as a threat to your organization.
How It Works
Common Uses
Automate IOC enrichment and alert prioritization
Enrich and prioritize SIEM alerts
Learning resources
Enrich and prioritize SIEM alerts
Respond to incidents with confidence
Empower Incident response (IR) and Forensic capabilities
Learning resources
Empower Incident response (IR) and Forensic capabilities
Threat intelligence and advanced hunting
Efficiently hunt for threats
Learning resources
Efficiently hunt for threats
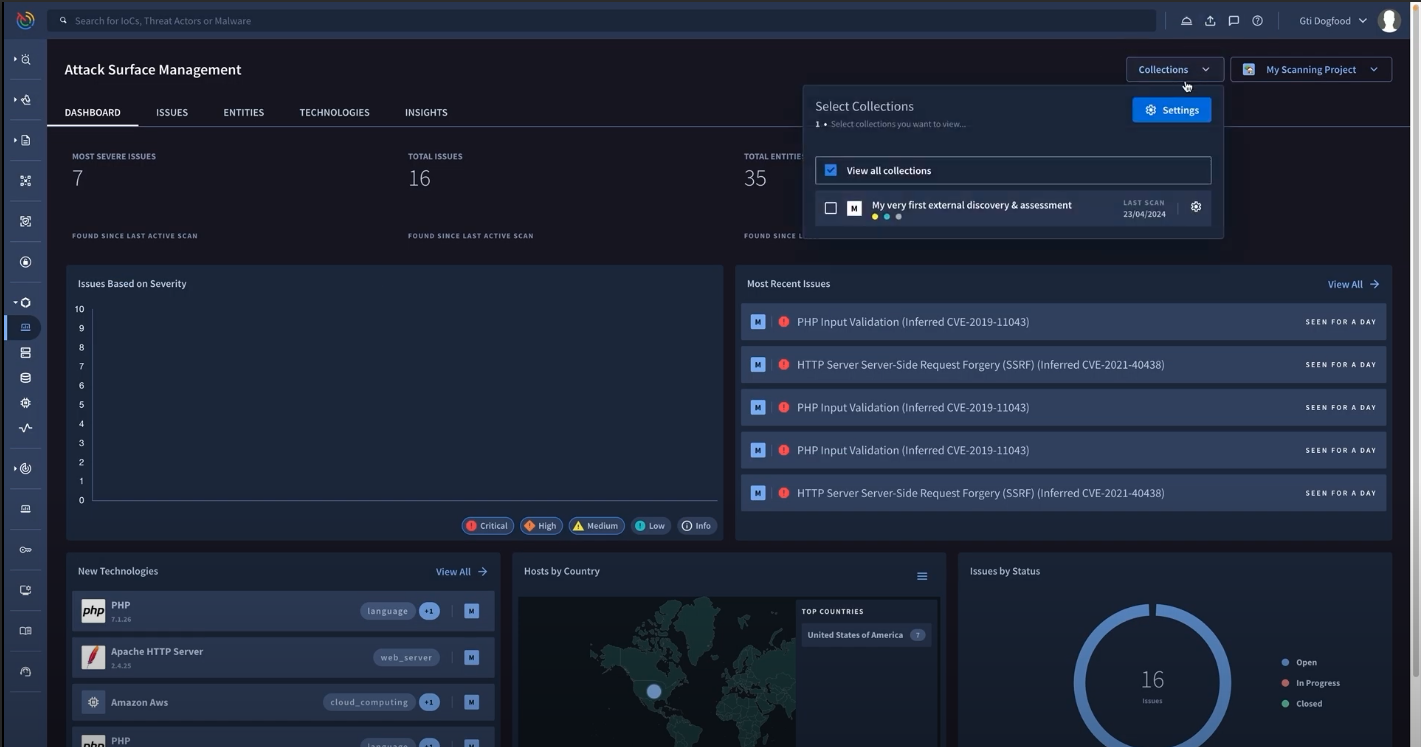
Uncover external threats
Stay ahead of the threats
Learning resources
Stay ahead of the threats
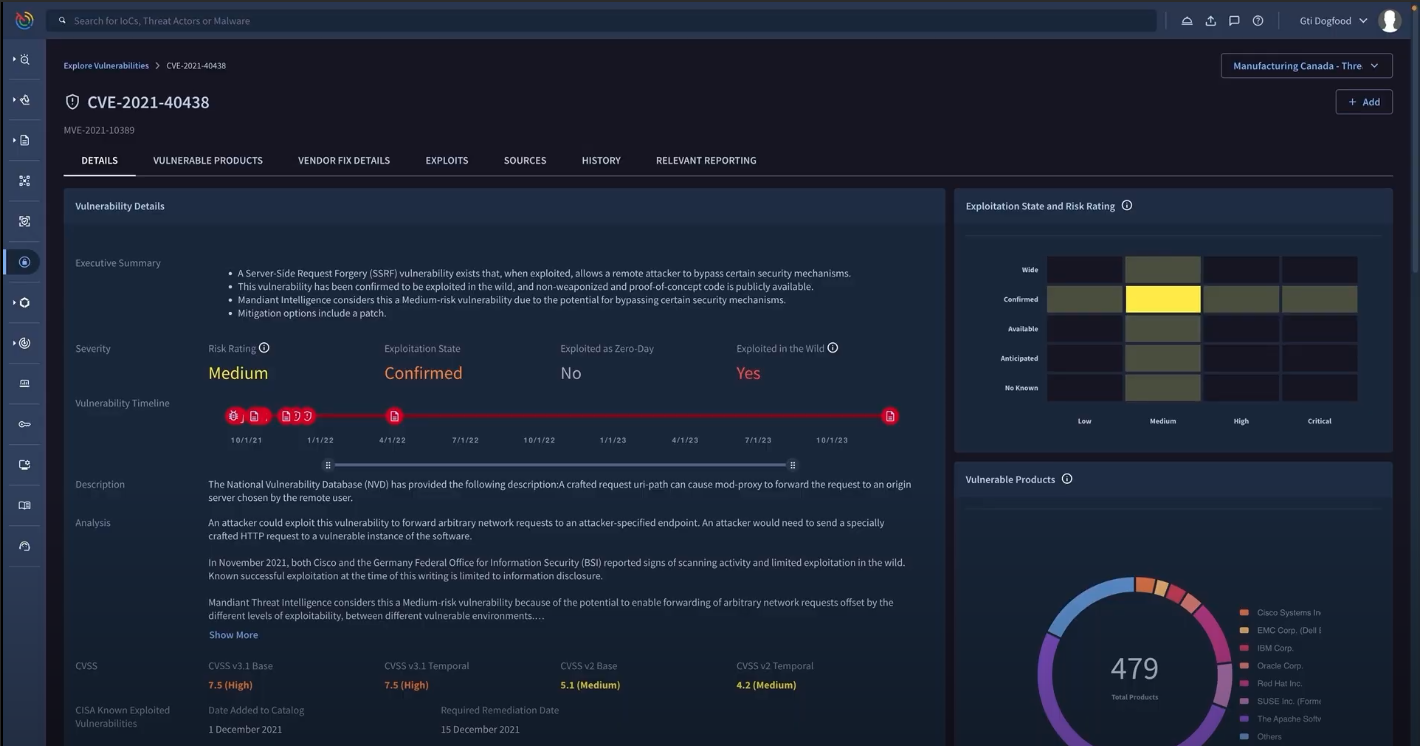
Optimized vulnerability management
Put our resources where they are most needed
Learning resources
Put our resources where they are most needed
AI-driven threat intelligence
Know and track the biggest threats to your org everyday
Learning resources
Know and track the biggest threats to your org everyday
Understand threat intel faster with AI generated summaries
Leverage the power of Gemini in Threat Intelligence
Learning resources
Leverage the power of Gemini in Threat Intelligence
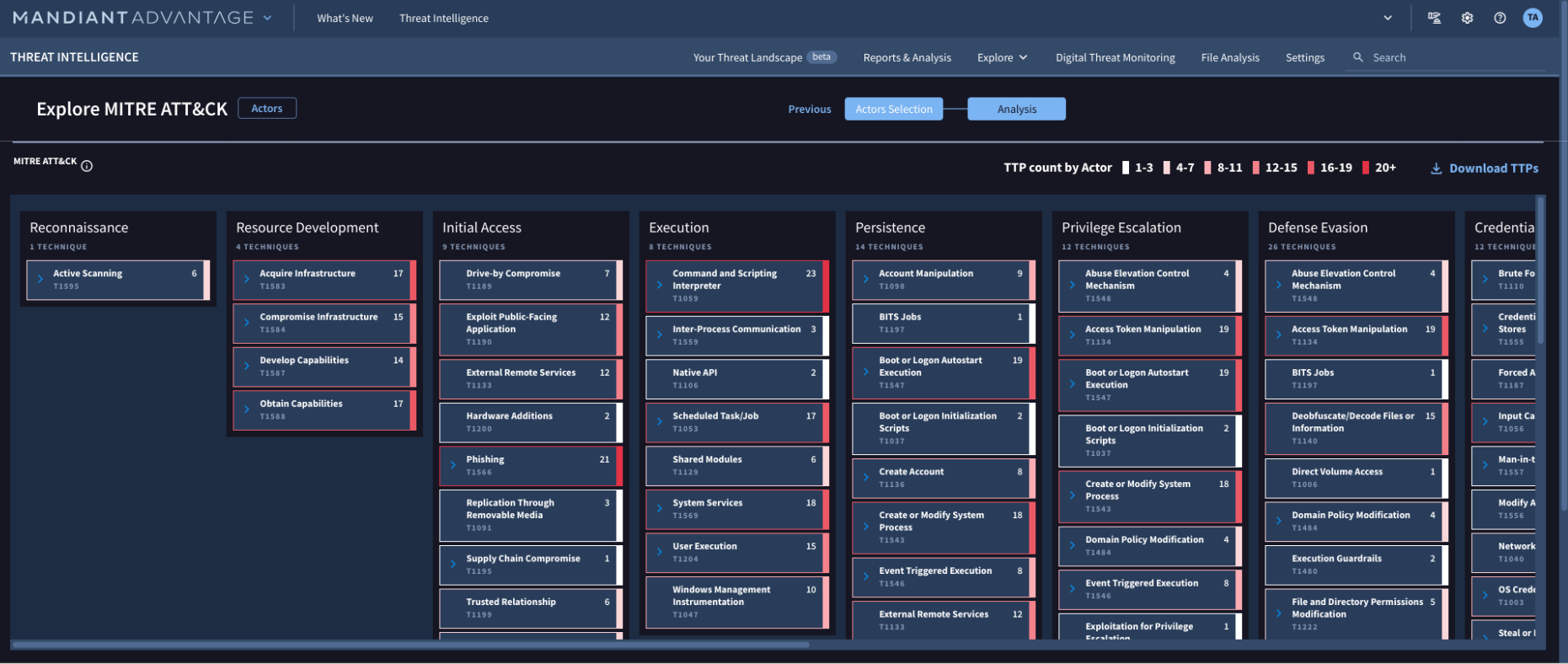
Get visibility into the threat actor’s playbook
Know how the attack will happen before it starts
Learning resources
Know how the attack will happen before it starts
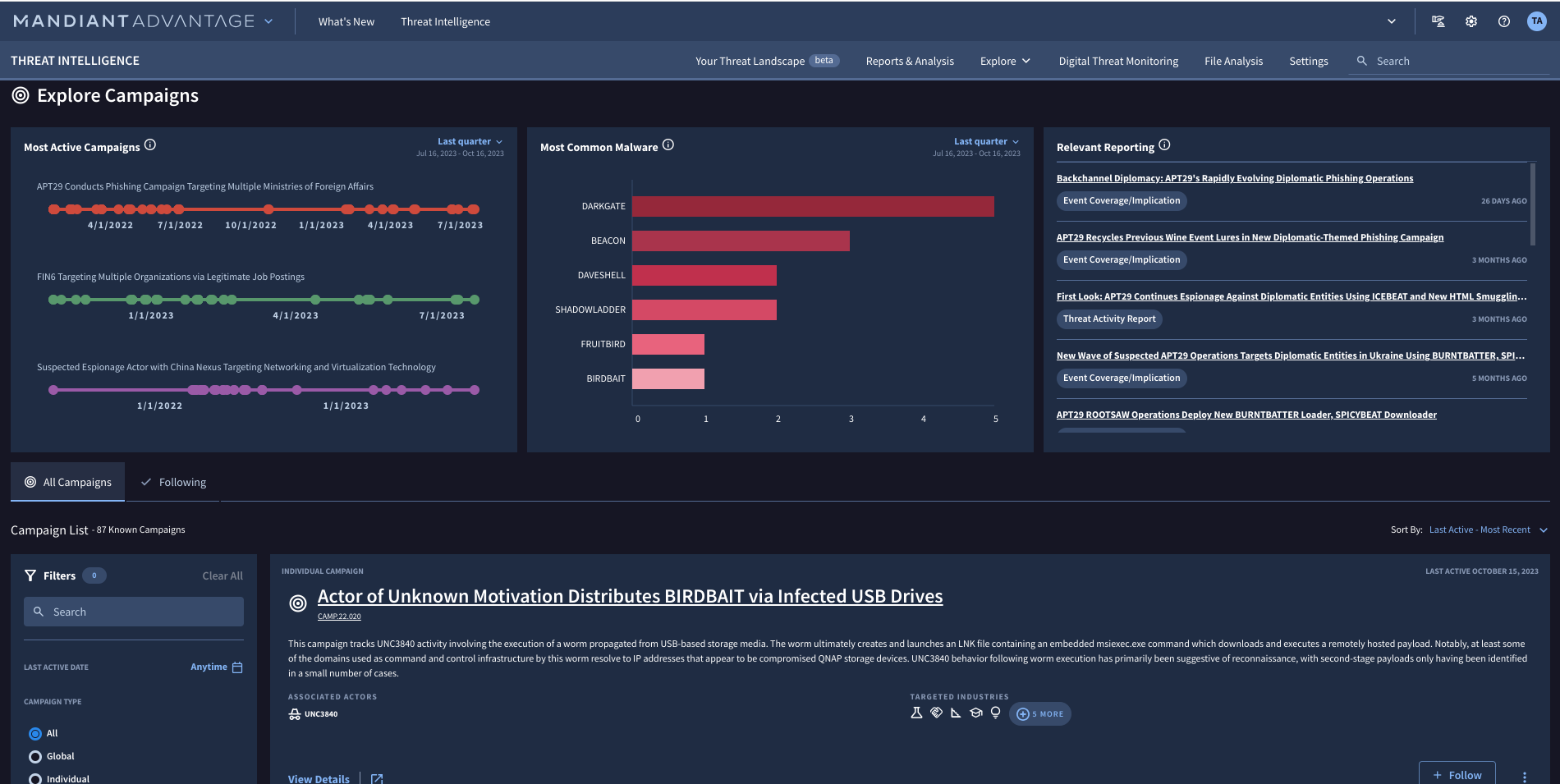
Anticipate, identify and respond to threats with confidence
Visibility into active threat campaigns
Learning resources
Visibility into active threat campaigns
OEM Google Threat Intelligence
Make Google Threat Intelligence a part of your offering
Learning resources
Make Google Threat Intelligence a part of your offering
Pricing
| How Google Threat Intelligence pricing works | Subscriptions are priced on a flat annual rate with a set number of API calls per subscription level. More API call packs can be added separately. | |
|---|---|---|
| Product/subscription | Description | Pricing |
Google Threat Intelligence - Standard | For organisations looking for threat intelligence driven event triage and detections to improve their security posture. | |
Google Threat Intelligence - Enterprise | For organizations who want to use threat intelligence to be more proactive, know more about threat actors targeting them and conduct efficient hunting exercises. | |
Google Threat Intelligence - Enterprise+ | For organizations with a strong cyber threat intelligence teams who see threat intelligence as a critical tool to understand and stay ahead of their adversaries. | |
Google Threat Intelligence - OEM | For Technology vendors looking to help their customers stay ahead of adversaries with Google Threat Intelligence. | |
How Google Threat Intelligence pricing works
Subscriptions are priced on a flat annual rate with a set number of API calls per subscription level. More API call packs can be added separately.
Google Threat Intelligence - Standard
For organisations looking for threat intelligence driven event triage and detections to improve their security posture.
Google Threat Intelligence - Enterprise
For organizations who want to use threat intelligence to be more proactive, know more about threat actors targeting them and conduct efficient hunting exercises.
Google Threat Intelligence - Enterprise+
For organizations with a strong cyber threat intelligence teams who see threat intelligence as a critical tool to understand and stay ahead of their adversaries.
Google Threat Intelligence - OEM
For Technology vendors looking to help their customers stay ahead of adversaries with Google Threat Intelligence.
FAQ
What is cyber threat intelligence (CTI)?
CTI is a refined insight into cyber threats. Intelligence teams use credible insights from multiple sources to create actionable context on the threat landscape, threat actors and their tactics, techniques, and procedures (TTPs). The effective use of CTI allows organizations to make the shift from being reactive to becoming more proactive against threat actors.
How can CTI be used to make security more proactive?
Credible threat intelligence can be used to understand the malware and TTPs threat actors use and the vulnerabilities they exploit to target specific industries and regions. Organizations use this intelligence to implement, configure, and adjust security tools, and train staff to thwart attacks.
What is a threat actor?
A threat actor is a person or group of people who conduct malicious targeting or attacks on others. Typically motivated by espionage, financial gain, or publicity, threat actors may conduct a full campaign alone or work with other groups who specialize in specific aspects of an attack.
How can you identify active threats?
Assuming we all agree that a “threat” is defined as a plan or inclination to attack as opposed to an “attack” which is an existing or previously successful breach. Identifying active threats can be done using threat intelligence which will help provide context into the threat actors and malware impacting your specific region or industry. Another method to identify active threats is by scanning the open, deep, and dark web for chatter around your organization, personnel, technology, or partners. By identifying these threats, security professionals can proactively adjust their defenses to block or reduce the impact of a potential attack.
What are the three types of CTI?
Strategic – High level trends used to drive business decisions and security investments.
Operational – Contextual information on impending threats to the organization, used by security professionals to understand more about threat actors and their TTPs.
Tactical – Understanding of the threat actor TTPs, used by security professionals to stop incidents and make defensive adjustments.