Sensitive Data Protection
Discover and protect your sensitive data
A fully managed service designed to help you discover, classify, and protect your valuable data assets with ease.
Try our discovery service for BigQuery by scanning and profiling a single table of your choice.
Features
Automated sensitive data discovery and classification
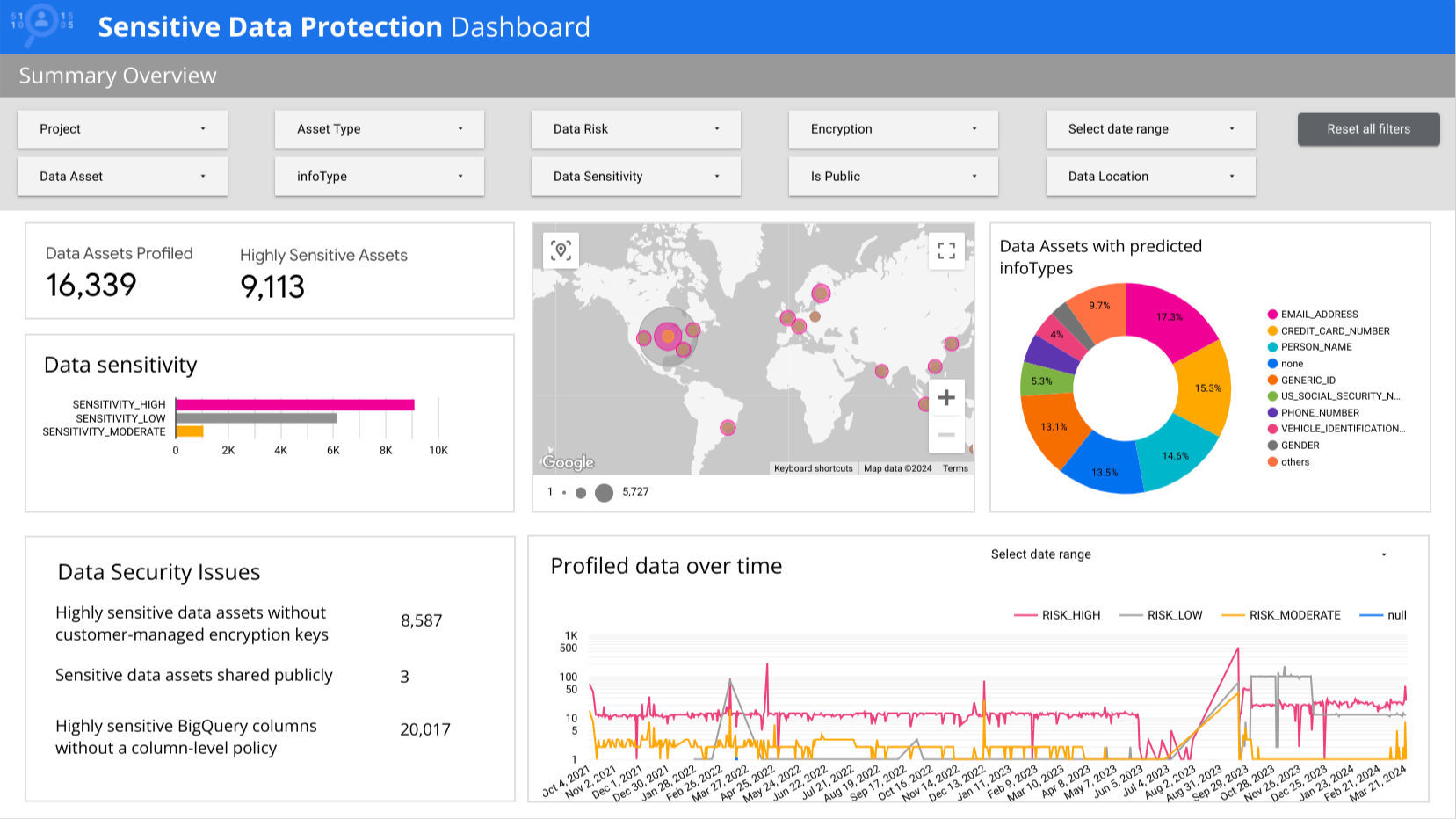
Continuously monitor your data assets across your entire organization, select organization folders, or individual projects. Powerful and easy-to-use UI available in the cloud console. Use data asset profiles to inform your security, privacy, and compliance posture. Choose from 200+ predefined detectors or add your own custom types, adjust detection thresholds, and create detection rules to fit your needs and reduce noise.
Sensitive data intelligence for security assessments
Sensitive Data Protection is deeply integrated into the Security Command Center Enterprise risk engine. This powerful combination continuously monitors your data, pinpoints your high-value assets, analyzes vulnerabilities, and simulates real-world attack scenarios. With this intelligence, you can proactively address security, posture, and threat risks and safeguard the data that drives your business.
Powerful and flexible protection for your AI/ML workloads
Sensitive Data Protection provides tools to classify and de-identify sensitive elements or unwanted content within your data. This fine-grained data minimization can help you prepare data for AI model training or tuning and protect at run time in workloads like chat, data collection, data display, and generative AI prompts and responses to ensure you adhere to regulations and internal policies.
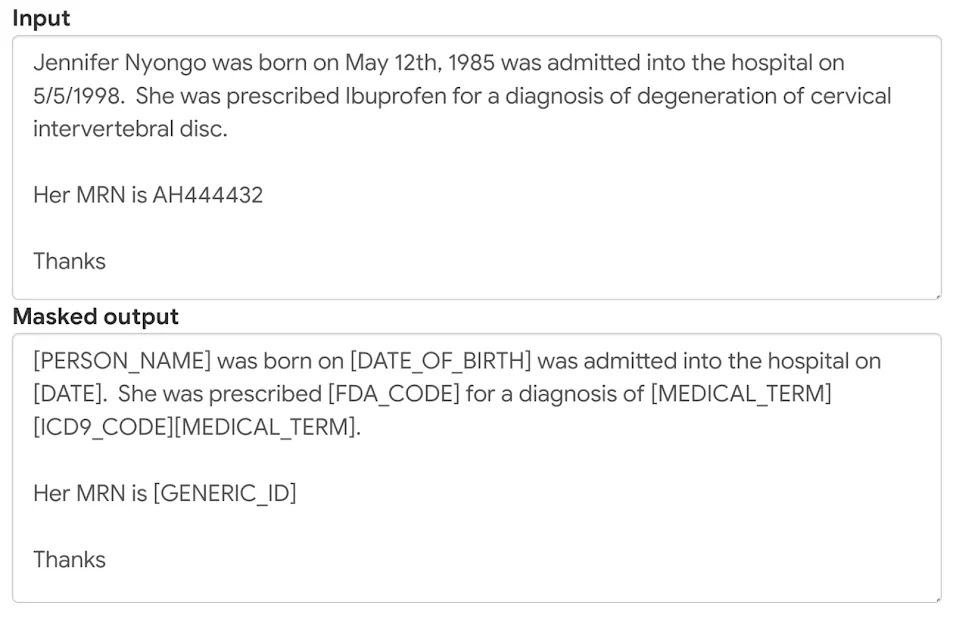
De-identification, masking, tokenization, and bucketing
Sensitive Data Protection helps you take a data-centric approach to securing your assets. De-identification enables you to transform your data to reduce data risk while retaining data utility. Additionally, you can use insights to apply column-level, fine-grained access, or dynamic masking policies.
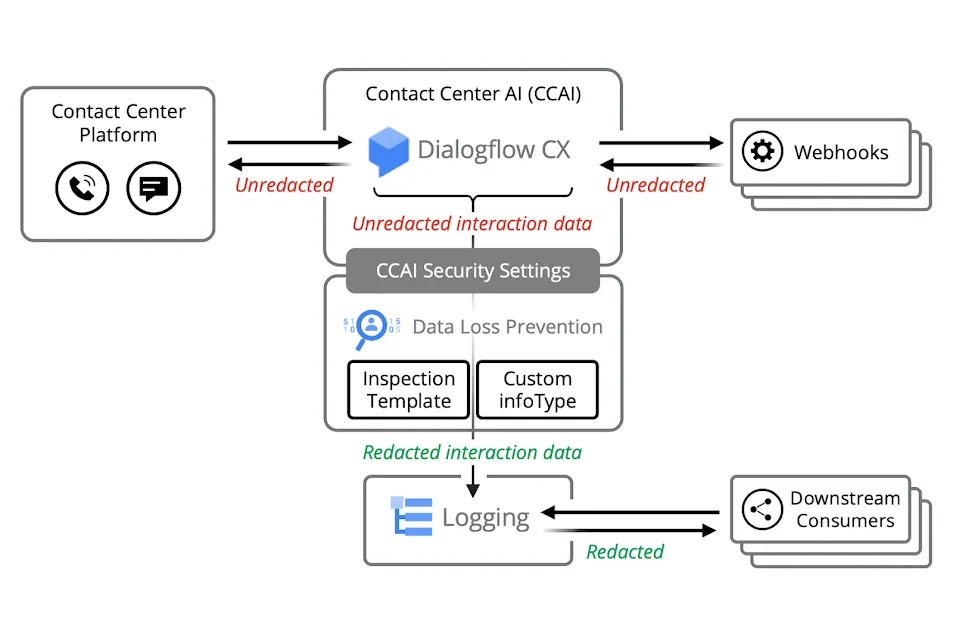
Cover use cases anywhere, on or off cloud with the DLP API
Cloud Data Loss Prevention and the DLP API are part of Sensitive Data Protection. Use the DLP API’s built-in support for various Google Cloud services. Additionally, the DLP API’s in-line content methods enable support for additional data sources, custom workloads, and applications on or off cloud.
Options table
| Service type | Description | Suggested use |
|---|---|---|
Sensitive data discovery | Used to discover, scan, and classify across a wide set of data | Monitoring for sensitive data across a large set of assets, such as your entire data warehouse |
Storage inspection | Targeted, focused inspection to help you find every data element in Google Cloud storage systems | Investigations or dealing with high-value unstructured data like chat logs stored in Google Cloud |
Hybrid inspection | Targeted, focused inspection to help you find every data element in storage systems outside Google Cloud | Investigations or dealing with high-value unstructured data like chat logs stored outside Google Cloud |
Content inspection | Synchronous, stateless inspection on data from anywhere | Inspecting in near real time or integrating into custom workloads, applications, or pipelines |
Content de-identification | Synchronous, stateless transformation on data from anywhere | Masking, tokenizing, de-identifying in near real time or integrating into custom workloads, applications, or pipelines |
Learn more about sensitive data discovery.
Sensitive data discovery
Used to discover, scan, and classify across a wide set of data
Monitoring for sensitive data across a large set of assets, such as your entire data warehouse
Storage inspection
Targeted, focused inspection to help you find every data element in Google Cloud storage systems
Investigations or dealing with high-value unstructured data like chat logs stored in Google Cloud
Hybrid inspection
Targeted, focused inspection to help you find every data element in storage systems outside Google Cloud
Investigations or dealing with high-value unstructured data like chat logs stored outside Google Cloud
Content inspection
Synchronous, stateless inspection on data from anywhere
Inspecting in near real time or integrating into custom workloads, applications, or pipelines
Content de-identification
Synchronous, stateless transformation on data from anywhere
Masking, tokenizing, de-identifying in near real time or integrating into custom workloads, applications, or pipelines
Learn more about sensitive data discovery.
Common Uses
Gain awareness of your sensitive data
Discovery: Continuous visibility into your sensitive data
Discovery: Continuous visibility into your sensitive data
Understand and manage your data risk across your organization. Continuous data monitoring across your organization can help you make more informed decisions, manage and reduce your data risk, and stay in compliance. With no jobs or overhead to manage, you can focus on the outcomes and your business.
Tutorials, quickstarts, & labs
Discovery: Continuous visibility into your sensitive data
Discovery: Continuous visibility into your sensitive data
Understand and manage your data risk across your organization. Continuous data monitoring across your organization can help you make more informed decisions, manage and reduce your data risk, and stay in compliance. With no jobs or overhead to manage, you can focus on the outcomes and your business.
Investigate your storage
Deep inspection of structured and unstructured data
Deep inspection of structured and unstructured data
Inspect your data in storage systems exhaustively and investigate individual findings.
Tutorials, quickstarts, & labs
Deep inspection of structured and unstructured data
Deep inspection of structured and unstructured data
Inspect your data in storage systems exhaustively and investigate individual findings.
Understand sensitive anomalies
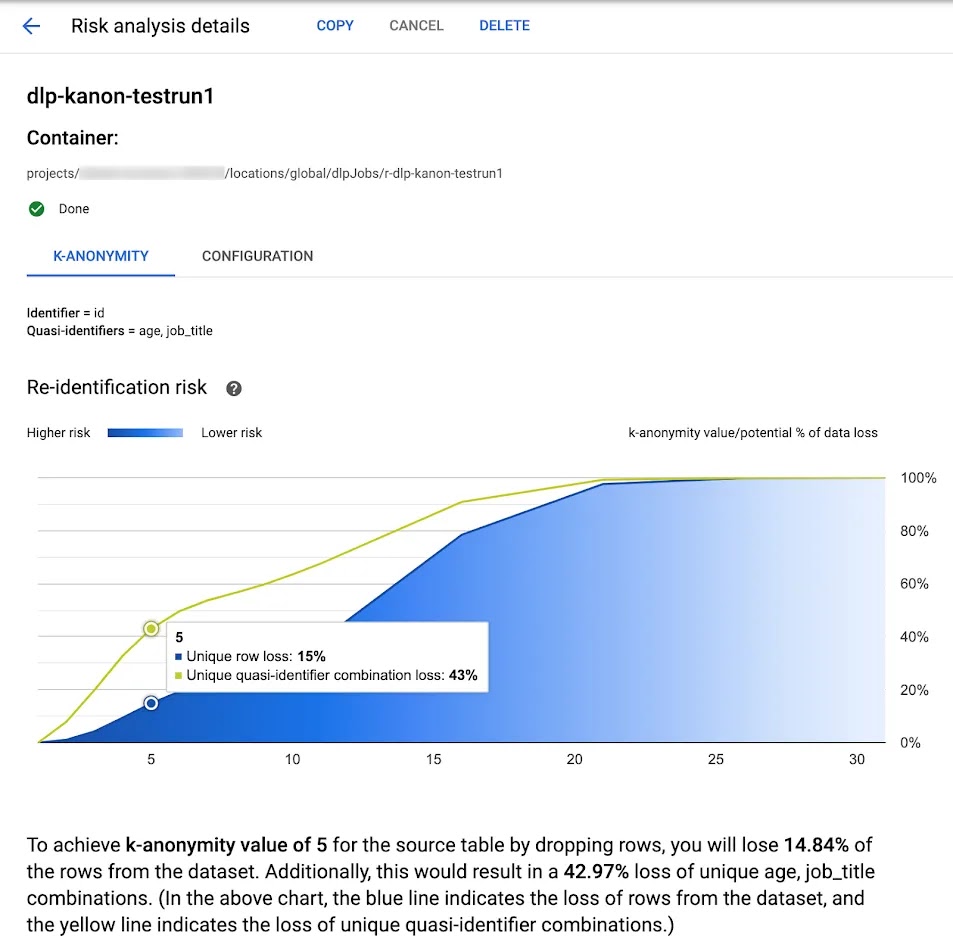
Privacy risk analysis of your data
Privacy risk analysis of your data
Assess data for privacy and re-identification risk. Risk analyses can help you see how the size, shape, and distribution of data can increase re-identification risk.
Tutorials, quickstarts, & labs
Privacy risk analysis of your data
Privacy risk analysis of your data
Assess data for privacy and re-identification risk. Risk analyses can help you see how the size, shape, and distribution of data can increase re-identification risk.
Automate de-identification
Advanced masking and de-identification
De-identify: Redact and tokenize data
Protect sensitive data as you migrate to the cloud
Protect sensitive data as you migrate to the cloud
Unblock more workloads as you migrate to the cloud. Sensitive Data Protection helps you inspect and classify your sensitive data in structured and unstructured workloads. De-identification techniques like tokenization (pseudonymization) let you preserve the utility of your data for joining or analytics, while reducing the risk of handling the data, by obfuscating the raw sensitive identifiers.
Tutorials, quickstarts, & labs
Protect sensitive data as you migrate to the cloud
Protect sensitive data as you migrate to the cloud
Unblock more workloads as you migrate to the cloud. Sensitive Data Protection helps you inspect and classify your sensitive data in structured and unstructured workloads. De-identification techniques like tokenization (pseudonymization) let you preserve the utility of your data for joining or analytics, while reducing the risk of handling the data, by obfuscating the raw sensitive identifiers.
Protect high-value AI and ML workloads
Prepare data for model training
Prepare data for model training
Find and remove sensitive elements from your data before model training. Tailor this to your business needs with full control over the data types to remove or keep.
Tutorials, quickstarts, & labs
Prepare data for model training
Prepare data for model training
Find and remove sensitive elements from your data before model training. Tailor this to your business needs with full control over the data types to remove or keep.
Redact sensitive data elements in chat
Pricing
| How our pricing works | Discovery is billed based on the pricing mode you select. Inspection and transformation pricing is based on total bytes processed. | |
|---|---|---|
| Category or type | Description | Price USD |
Discovery | Consumption mode | $0.03/GB |
Fixed-rate subscription mode A default discovery subscription is included at no charge with the purchase of a Security Command Center Enterprise subscription. | $2500/unit | |
Inspection and transformation | Up to 1 GB | Free |
Inspection of Google Cloud storage systems | Starting at $1/GB Lower with volume | |
Inspection of data from any source (hybrid inspection) | Starting at $3/GB Lower with volume | |
In-line content inspection | Starting at $3/GB Lower with volume | |
In-line content de-identification | Starting at $2/GB Lower with volume | |
Risk analysis | Analyze sensitive data to find properties that might increase the risk of subjects being identified | No Sensitive Data Protection charges* Risk analysis uses resources in BigQuery; charges appear as BigQuery usage |
Learn more about Sensitive Data Protection pricing.
How our pricing works
Discovery is billed based on the pricing mode you select. Inspection and transformation pricing is based on total bytes processed.
Discovery
Consumption mode
$0.03/GB
Fixed-rate subscription mode
A default discovery subscription is included at no charge with the purchase of a Security Command Center Enterprise subscription.
$2500/unit
Inspection and transformation
Up to 1 GB
Free
Inspection of Google Cloud storage systems
Starting at
$1/GB
Lower with volume
Inspection of data from any source (hybrid inspection)
Starting at
$3/GB
Lower with volume
In-line content inspection
Starting at
$3/GB
Lower with volume
In-line content de-identification
Starting at
$2/GB
Lower with volume
Risk analysis
Analyze sensitive data to find properties that might increase the risk of subjects being identified
No Sensitive Data Protection charges*
Risk analysis uses resources in BigQuery; charges appear as BigQuery usage
Learn more about Sensitive Data Protection pricing.
Business Case
Explore how other businesses cut costs, increase ROI, and drive innovation with Sensitive Data Protection
Partners & Integration