Secure Web Proxy
Monitor and secure egress web traffic to help protect cloud workloads.
Proxy traffic from cloud workloads to the internet
Restrict outbound traffic to trusted web services
Investigate security events and incidents involving egress traffic
Benefits
Web traffic inspection and protection
Web traffic inspection and protection
Protects cloud workloads from malicious activity by inspecting web traffic, blocking untrusted web services, and logging egress traffic for forensic analysis.
Easy to deploy and manage
Easy to deploy and manage
Requires no virtual machines (VMs) to set up or configure, and doesn’t require software updates to maintain security. It works out of the box.
Implement zero-trust principles
Implement zero-trust principles
Helps organizations implement zero-trust principles by default—denying web egress traffic and allowing workloads to access only trusted web services.
Key features
Key features
Granular egress access policies
Secure Web Proxy (Cloud SWP) enables organizations to enforce granular access policies, limiting egress web traffic based on source, identities (secure tags, service accounts), destinations, and requests types (methods, headers, URLs). The URLs in policies can be specified by using lists, wildcards, or patterns.
TLS inspection
Secure Web Proxy offers a scalable TLS inspection service that lets you intercept TLS traffic, inspect the encrypted request, and enforce your policies. Cloud SWP uses Certificate Authority Service (CAS) to generate the certificates used for TLS inspection.
Modular deployment
Secure Web Proxy instances, policies, and URL lists are all modular objects that can be created or reused by distinct administrators. For example, you can deploy multiple Secure Web Proxy instances that all use the same proxy policy.
Secure Web Proxy has helped us to improve our security in Google Cloud. We are now able to filter outbound HTTP and HTTPS traffic from our applications. In addition, having a native solution will allow us to replace the VM-based solution we currently have, providing us with cost savings and continuing to deliver on our strategy of replacing products with cloud native services.
Roberto Vega, Cloud analyst, Carrefour

Documentation
Documentation
Use cases
Use cases
Restrict access to trusted external web services
Secure Web Proxy lets you apply granular access policies to your egress web traffic so that you can secure your network. This allows you to programmatically restrict cloud workload access to only trusted external web services.
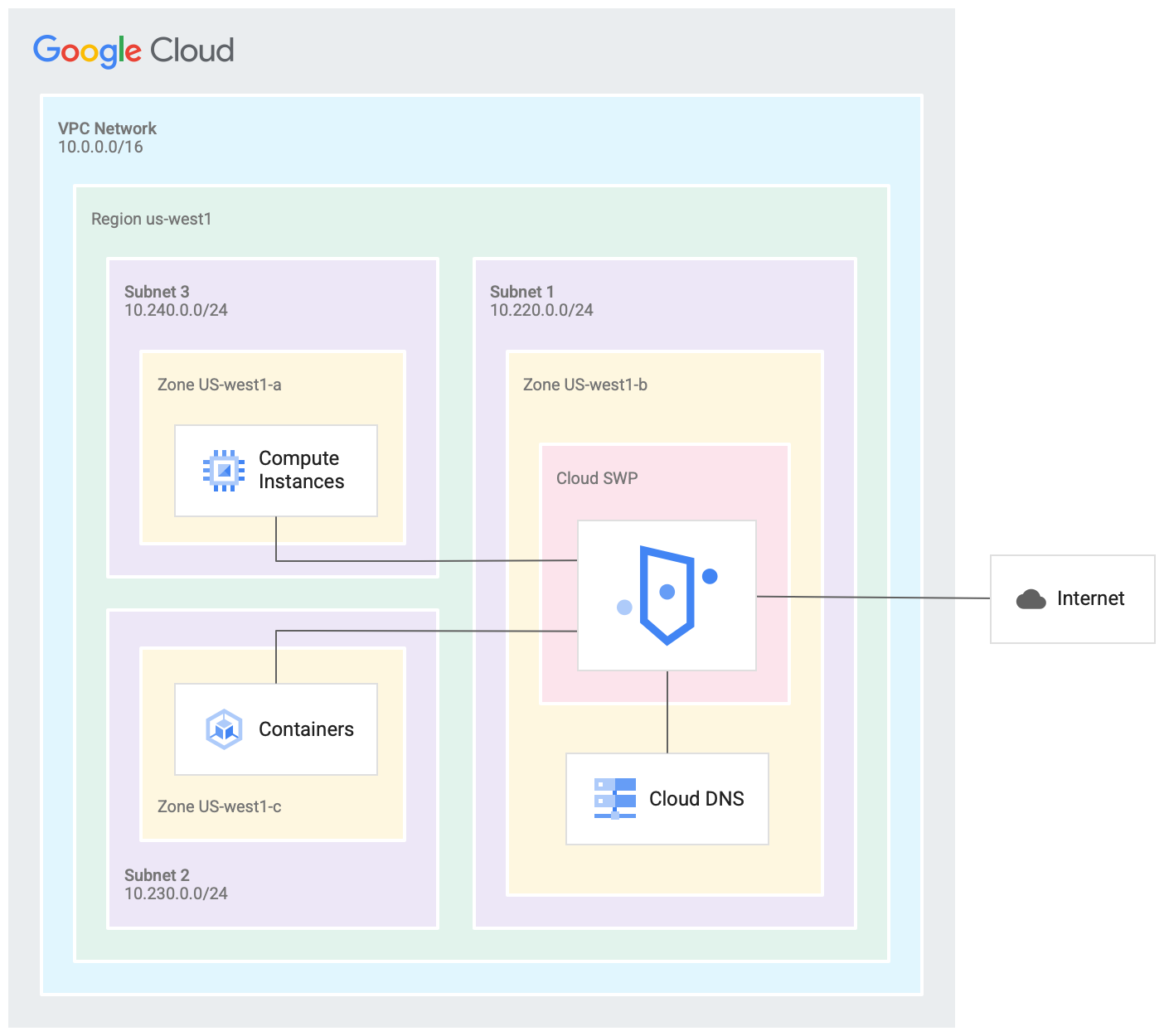
Monitor outbound access and investigate incidents
Secure Web Proxy monitors outbound access and identifies traffic that doesn't conform to policy and logs it to Cloud Logging. This allows you to monitor internet usage, discover threats to your network by spotting command and control (C2C) traffic or anomalous data transfers. Logs can also be used in forensics to investigate security events and incidents involving egress web traffic.
Take the next step
Start building on Google Cloud with $300 in free credits and 20+ always free products.
Need help getting started?
Contact salesWork with a trusted partner
Find a partnerContinue browsing
See all products












