Extend Chrome security reporting to CrowdStrike Falcon LogScale

Fletcher Oliver
Chrome Enterprise Customer Engineer
Chrome + CrowdStrike integration is available now
Security insights are a critical piece of a secure enterprise browsing solution. Integrating your chosen security solution with Chrome, made possible by Chrome Enterprise Connectors Framework, gives IT and security teams a birds-eye view of the potential threats users face on the web and make data-driven decisions in their security journey.
We're pleased to share that the Chrome and CrowdStrike Falcon LogScale integration is now available in the Google Admin console in Chrome Browser Cloud Management. Organizations can now easily set up the integration to extract and analyze insights from security events within managed Chrome browsers.
Available Security Events
Malware transfer
Password changed
Unapproved password reuse
Unsafe site visit
Log-in events
Password breaches
Extension installs (coming soon)
Crash events (coming soon)
Enrolling machines in Chrome Browser Cloud Management
Getting started is easy. The first step is to make sure Chrome Browser Cloud Management is set up for your organization. This tool helps manage Chrome browser from a single, cloud-based Admin console across Windows, Mac, Linux, Android and iOS at no additional cost. This is the same console where IT teams can also manage Chrome OS.
Check out this guide for steps on how to enroll your devices. Once you are done, or if you already have Chrome Browser Cloud Management in place, move to the steps below.
Setup in CrowdStrike Falcon LogScale instance
Log into your CrowdStrike Falcon LogScale instance.
You will need to create a new repository for your Google Chrome data.
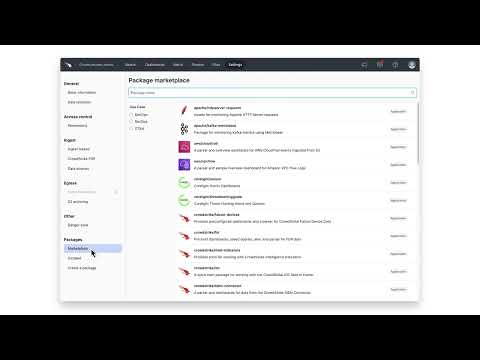
Once you've created a new repository, under packages, click on the Marketplace section.
Search for Chrome, then install the CrowdStrike Falcon LogScale package for google/chrome-enterprise. When choosing the package, the README provides information about the package contents and other related information.
After installing the package, under Ingest, click on Ingest tokens and click the Add token button. Give it a name and type in Chrome under the assigned parsers.
Select the Google_Chrome_Enterprise parser. Click on the eye icon to bring up the token value.
Hit the copy button and save the token value, as you will be entering this into the admin console in the following section
Setup in Chrome Browser Cloud Management


Log into the Google Admin console at admin.google.com and select the organizational unit containing the enrolled browsers you want to send security events to CrowdStrike.
Navigate to Devices>Chrome>Users and browsers. Add a filter for “event reporting.”
Under events reporting, select Enable event reporting. Under the additional settings, you can specify which events you want to send to CrowdStrike.
Now that the events are turned on, click on the blue hyperlink called “Reporting connector provider configurations” to take you to the connector provider configurations, or it can be found under Devices>Chrome>Connectors.
Click the New Provider Configuration button and select CrowdStrike as the provider.
Enter the configuration name that you want this connector to display as in the Google Admin console.
Enter the host name of your CrowdStrike instance (most likely cloud.us.humio.com or sa-cluster.humio-support.com or your on-prem instance) and the ingest token value from step 7 of the last section
Press the Add Configuration to save.
Select the Organizational Unit where the reporting events are turned on, select the Chrome CrowdStrike connector created in the previous step, and hit Save.
You can also download the setup guide here or watch the setup of integration with CrowdStrike Falcon LogScale end-to-end in the video below:
Chrome is continuously working with other partners to expand the security ecosystem to help businesses work safer on the web. Learn more about Chrome browser security.



